Hacker

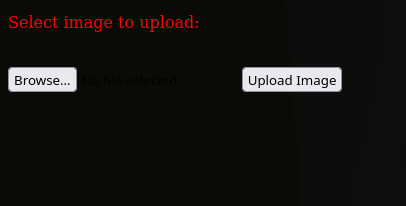
Hacker Sounds badass right ? yep it is but this was quite easy Heading onto the website we were greeted with a website and all it does is to upload a file
File upload vulnerabilities are when a web server allows users to upload files to its filesystem without sufficiently validating things like their name, type, contents, or size.
Read more here

Here there are filters such as file type and size
- it must be a a jpeg image
- it must be 35 bytes or less
Bypassing this was easy we simply craft a really small php payload prepend it with a number of A’s then using hexedit we change the hex character, for jpeg files the magic byte is
FFD8, I prepended 4 A’s in Hex A is 41 (remember your ascii table)
Let’s dive into it my payload was really tiny(typing it out will mess up my md file)

AAAA<?=$_GET[0]?>
saving that and then checking the file type we see it’s ascii text


Now we edit the hex character to that of a jpeg


checking the file type again we see it has changed

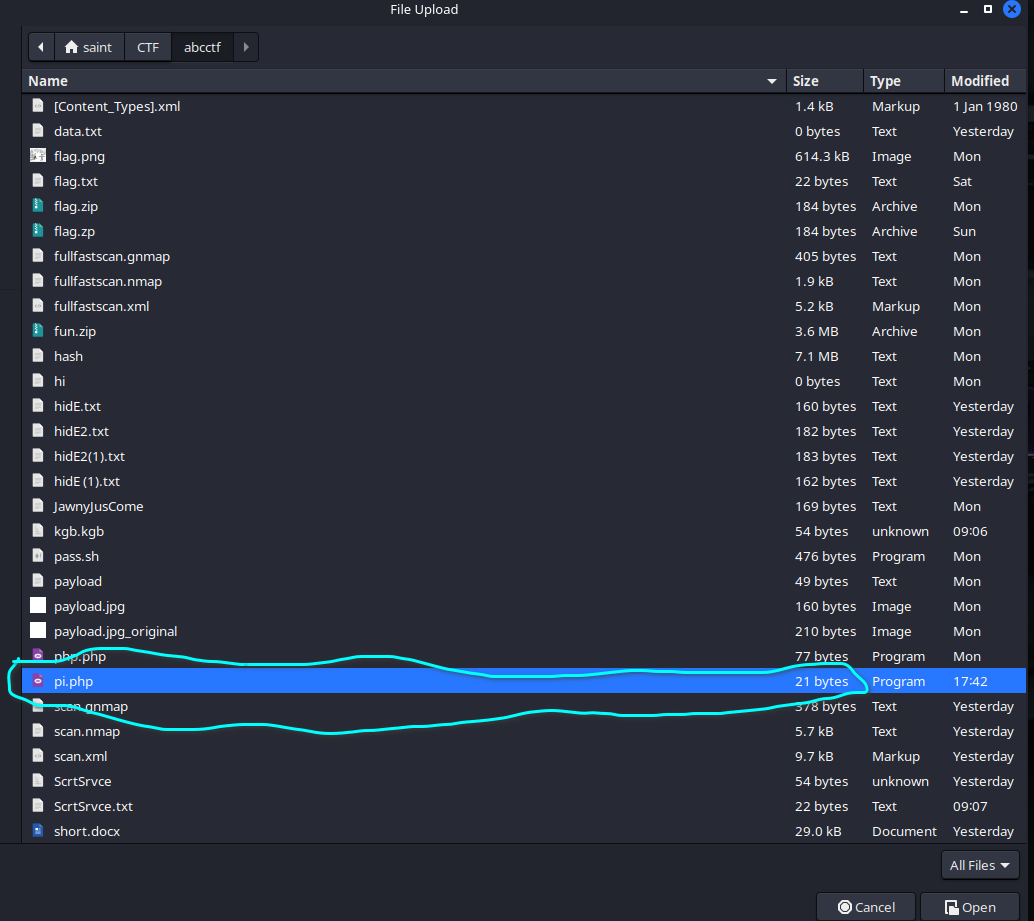
So now we upload our shell

While it’s possible to guess the file path running a directory fuzzing helps know the files and directories on the web server


running curl does the same thing

It did take a while finding our flag but yh we did find it in upload.php

So that’s that